The first 60 days of a Managed SOC engagement are critical because this period sets the foundation for your organization’s long-term security posture. How the SOC is onboarded, integrated, and tuned during this window determines how quickly threats can be detected, incidents can be responded to, and compliance requirements can be met. A poorly executed initial phase can create blind spots, delays, and operational inefficiencies that affect your entire security strategy.
This guide is designed for small and mid-market businesses (SMBs) looking to outsource security operations, IT and security teams responsible for implementing and managing SOC integrations, C-level executives (CIOs, CTOs, CISOs) who need to understand business impact, managed service providers (MSPs) and security partners coordinating client deployments, and compliance teams in regulated industries who need audit-ready reporting.
By the end of this article, you’ll have a clear understanding of what to expect in the first 60 days, including actionable milestones, deliverables, and operational readiness checkpoints. This ensures your organization gets the maximum value from its Managed SOC engagement while minimizing risk and accelerating threat detection and response.
Pre-Onboarding Preparation (Before Day 1)
Before your Managed SOC engagement officially begins, proper preparation is key to ensure a smooth and efficient deployment. Skipping or delaying pre-onboarding tasks can lead to delays, misconfigurations, and gaps in monitoring. Here’s what your organization needs to have ready:
1. Required Access and Credentials
Your SOC provider will need secure access to your systems, network devices, cloud environments, and applications. This includes:
- Admin or read-only credentials for key servers, firewalls, and endpoints.
- API access for cloud platforms and SaaS applications.
- VPN or secure remote access for monitoring tools.
Ensuring these are ready ahead of time prevents delays during tool deployment and log collection.
2. Priority Log Sources and Infrastructure Readiness
Identify which log sources and systems are critical for security monitoring. This typically includes:
- Network firewalls, routers, and switches.
- Servers, endpoints, and critical applications.
- Cloud platforms and SaaS applications (Office 365, AWS, Azure, etc.).
- Security tools like EDR, vulnerability scanners, and threat intelligence feeds.
Having this list prepared ensures the SOC team can integrate and monitor these sources from day one.
3. Internal Stakeholders and Responsibilities
Assign key internal stakeholders who will collaborate with the SOC provider. These roles often include:
- IT administrators for access and configuration support.
- Security officers for policy and compliance oversight.
- The business unit leads to providing context for critical assets.
Clearly defining responsibilities ensures accountability and smooth communication throughout the first 60 days.
4. Compliance Requirements and Documentation
Provide all necessary compliance and regulatory documentation to align SOC activities with your obligations, such as:
- GDPR, HIPAA, SOC2, ISO27001 requirements.
- Internal security policies and standards.
- Existing incident response playbooks or risk assessments.
This allows the SOC team to tailor monitoring and reporting to your compliance needs from day one.
5. Importance of Preparing the Environment
A well-prepared environment accelerates SOC deployment, reduces configuration errors, and ensures early visibility into potential threats. By completing these pre-onboarding steps, you set the stage for a successful first 60 days, enabling faster monitoring, alerting, and response.
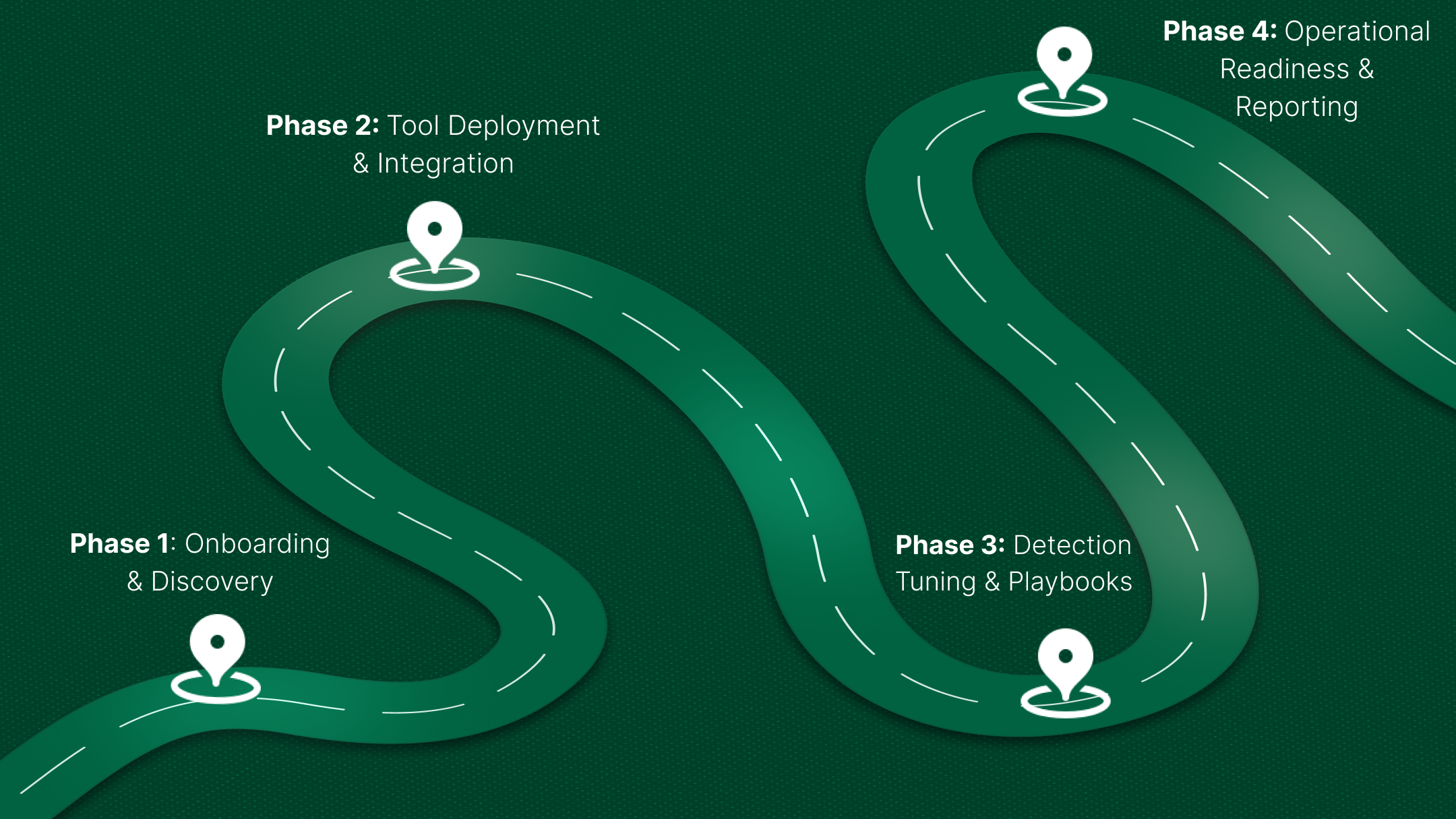
Phase 1 – Days 1–15: Onboarding & Discovery
The first 15 days of a Managed SOC engagement are all about understanding your environment, identifying priorities, and establishing a foundation for ongoing monitoring and incident response. A structured onboarding and discovery phase ensures that the SOC team has the right context to detect threats accurately and respond efficiently.
1. Assess Assets, Environment, and Current Security Posture
The SOC team will perform a thorough assessment of your infrastructure, including:
- Inventory of servers, endpoints, network devices, and cloud assets.
- Identification of critical business applications and data.
- Review of existing security tools and configurations.
- Evaluation of current threat landscape and known vulnerabilities.
This assessment helps identify gaps, prioritize monitoring, and shape the initial SOC deployment strategy.
2. Define Roles, Responsibilities, and Communication Channels
Clear responsibilities between your internal team and the SOC provider are essential for smooth collaboration. During this phase:
- Assign point-of-contact personnel for IT, security, and compliance.
- Establish communication channels for daily updates, escalations, and approvals.
- Define escalation paths for incidents and unusual alerts.
Setting expectations early ensures accountability and minimizes confusion throughout the first 60 days.
3. Document Policies, Compliance Gaps, and Existing Workflows
Understanding your policies and compliance requirements allows the SOC team to align monitoring and reporting with business needs:
- Collect existing security policies, standards, and workflows.
- Identify compliance gaps that may affect monitoring or reporting (e.g., SOC2, ISO27001, HIPAA).
- Map workflows for incident response, change management, and alert handling.
Documenting these elements ensures the SOC can enforce consistent processes from day one.
4. Deliverables & Success Criteria
By the end of the first 15 days, the following should be completed:
Completing these tasks sets a strong foundation for the next phase, ensuring the SOC is prepared to integrate tools, start monitoring, and tune detection rules effectively.
Phase 2 – Days 16–30: Tool Deployment & Integration
During days 16 to 30, the SOC engagement focuses on deploying security tools, integrating data sources, and establishing initial monitoring capabilities. This phase transforms the discovery insights into actionable monitoring and detection.
1. Deploy SIEM, Endpoint Detection, Log Collectors, and Monitoring Tools
The SOC team will deploy and configure the necessary security infrastructure:
- SIEM (Security Information and Event Management): Centralized logging and correlation.
- Endpoint Detection & Response (EDR): Monitors endpoints for suspicious activity.
- Log collectors and connectors: Ensure all critical systems, servers, applications, and cloud services are sending logs.
- Additional monitoring tools: May include vulnerability scanners, threat intelligence feeds, or cloud security monitoring platforms.
Proper deployment ensures visibility into your entire IT environment from day one.
2. Integrate Log Sources and Configure Dashboards and Alerts
Once tools are deployed:
- Connect all identified log sources to the SIEM and monitoring platforms.
- Configure dashboards to display key metrics and alerts for critical assets.
- Set up alerting rules for common threat indicators, including initial thresholds for high-priority events.
This integration allows the SOC to start observing patterns, detecting anomalies, and responding to potential threats.
3. Begin Initial Tuning to Reduce False Positives
Initial alert tuning is critical to ensure the SOC team and your internal staff can focus on real threats:
- Adjust thresholds for alerts based on your environment.
- Suppress irrelevant events and reduce noise.
- Validate that critical alerts trigger appropriate workflows.
Early tuning prevents alert fatigue and establishes a reliable monitoring baseline.
4. Deliverables & Success Criteria
By the end of this phase, the following should be completed:
Completing this phase ensures your organization has real-time visibility into key systems and establishes the foundation for tuning detection rules and developing response playbooks in the next phase.
Phase 3 – Days 31–45: Detection Tuning & Playbooks
During days 31 to 45, the focus shifts from basic monitoring to fine-tuning detection and establishing effective response procedures. This phase ensures alerts are accurate, meaningful, and actionable, while preparing internal teams to work effectively with the SOC.
1. Refine Detection Rules and Tune Alerts for Accuracy
- Adjust detection rules based on insights from the first 30 days.
- Suppress unnecessary or low-priority alerts to reduce noise.
- Validate that high-priority alerts trigger immediate escalation and response.
- Monitor alert performance and make adjustments to improve mean time to detect (MTTD).
Accurate alerts reduce false positives and ensure that the SOC team focuses on real threats, improving operational efficiency.
2. Create and Validate Incident Response Playbooks
- Develop standardized playbooks for common incident types (malware, phishing, insider threats, etc.).
- Ensure playbooks outline step-by-step response actions, responsibilities, and escalation procedures.
- Validate playbooks through tabletop exercises or simulated incidents to confirm effectiveness.
Playbooks provide a structured approach to incident response, ensuring consistency and compliance.
3. Train Internal Teams on Workflows and Escalation Procedures
- Conduct training sessions for IT and security teams on SOC workflows and alert handling.
- Clarify escalation paths and roles during incidents.
- Reinforce how internal teams collaborate with the SOC for rapid response.
Well-trained staff ensures that alerts are handled efficiently and that response actions are timely.
4. Deliverables & Success Criteria
By the end of this phase, the following should be completed:
Completing this phase ensures that your organization moves from basic monitoring to proactive detection and structured incident response, setting the stage for full operational readiness in the next phase..
Phase 4 – Days 46–60: Operational Readiness & Reporting
The final phase of the first 60 days focuses on full operational readiness, ensuring your Managed SOC is delivering real-time monitoring, actionable insights, and compliance-aligned reporting. By this stage, your organization should be able to detect threats efficiently and respond according to established workflows.
1. 24/7 Monitoring Across All Critical Assets
- Ensure continuous monitoring of servers, endpoints, network devices, and cloud environments.
- Validate that all log sources are feeding into the SOC platform reliably.
- Confirm that alerts and escalations are functioning across all priority systems.
This guarantees that your organization has round-the-clock visibility into potential threats.
2. Operational Dashboards and KPI Reporting
- Dashboards display real-time metrics for system health, threat detection, and alert status.
- Key performance indicators (KPIs) such as Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), and SLA adherence are tracked and reported.
- Reports provide actionable insights to internal teams and stakeholders.
These dashboards and KPIs allow leadership to measure SOC effectiveness and operational maturity.
3. Compliance Reporting Readiness
- Ensure SOC reporting meets regulatory and internal compliance requirements.
- Validate audit-ready reports for standards such as SOC2, ISO27001, HIPAA, or industry-specific mandates.
- Document monitoring activities, incident handling, and escalation actions.
Compliance readiness ensures that your organization can satisfy auditors and regulatory bodies without delays.
4. Deliverables & Success Criteria
By the end of this phase, the following should be completed:
Completing this phase marks the successful establishment of a fully operational Managed SOC, providing continuous security visibility, actionable reporting, and compliance alignment. This sets the stage for ongoing optimization and long-term security improvement.
Communication & Review Cadence
Effective communication is critical during the first 60 days of a Managed SOC engagement. Establishing a consistent cadence ensures that all stakeholders are informed, aligned, and able to respond quickly to incidents or operational changes.
1. Weekly Review Meetings and Status Updates
- Conduct structured weekly meetings between your internal teams and the SOC provider.
- Review alerts, incidents, and progress against onboarding milestones.
- Discuss challenges, adjustments, and opportunities for improving monitoring accuracy.
Regular updates help maintain visibility into SOC activities and ensure the first 60 days stay on track.
2. Stakeholder Alignment Checkpoints
- Identify key stakeholders including IT administrators, security officers, and business leaders.
- Schedule checkpoints to review dashboards, KPI performance, and compliance reporting.
- Align on priorities for monitoring, escalation, and incident response improvements.
Stakeholder alignment ensures expectations are met and decisions can be made promptly without bottlenecks.
3. Escalation Paths and Feedback Loops
- Clearly define escalation procedures for critical alerts and incidents.
- Establish feedback loops to report SOC observations, tuning requirements, or process improvements.
- Ensure both internal teams and the SOC provider understand roles, responsibilities, and response timelines.
Properly defined escalation and feedback mechanisms reduce risk, accelerate incident resolution, and strengthen collaboration between your internal team and the SOC provider.
Common Onboarding Blockers & Risk Mitigation
Even with thorough preparation, some challenges can arise during the first 60 days of a Managed SOC engagement. Identifying these potential blockers early and knowing how to mitigate them ensures a smoother onboarding process and faster operational readiness.
1. Missing or Misconfigured Log Sources
- Issue: Critical systems may not be sending logs, or logs may be misconfigured, resulting in blind spots.
- Mitigation:
- Conduct an early log source inventory during pre-onboarding.
- Validate connectivity and log formats before full deployment.
- Use automated testing tools to confirm logs are reaching the SOC platform.
2. Delays in Permissions and Access
- Issue: Delays in providing credentials, API access, or administrative permissions can slow down tool deployment.
- Mitigation:
- Identify and assign internal owners for access approval in advance.
- Maintain a checklist of required credentials and access points.
- Schedule early validation to ensure access is granted before the SOC team begins monitoring.
3. Early False Positives or Mis-Tuned Alerts
- Issue: Initial alert configurations may generate excessive false positives, leading to alert fatigue and reduced effectiveness.
- Mitigation:
- Implement phased tuning of detection rules, starting with high-priority assets.
- Establish a feedback loop between the SOC and internal teams to adjust thresholds.
- Monitor alert quality daily and refine rules iteratively.
4. Proactively Addressing Blockers
- Maintain regular communication with the SOC provider to flag potential issues early.
- Track progress against a pre-defined onboarding checklist to ensure all steps are completed on time.
- Schedule periodic internal review sessions to resolve minor issues before they become delays.
By anticipating these common blockers and implementing mitigation strategies, your organization can maximize the efficiency and effectiveness of the first 60 days, ensuring faster threat detection, reliable alerting, and a strong foundation for operational readiness.
Deliverables & Performance Benchmarks
Tracking performance benchmarks during the first 60 days of a Managed SOC engagement helps ensure that your organization is progressing toward operational readiness, accurate monitoring, and compliance. Clear metrics allow stakeholders to measure success, identify gaps, and make data-driven decisions.
1. Timeline to First Alert
- Goal: Receive the first meaningful alerts from critical systems within the first 15–20 days.
- Why it matters: Confirms that log sources are integrated, tools are functioning correctly, and the SOC can detect potential threats.
2. Time to Stable Rule Tuning
- Goal: By day 30–45, detection rules should be tuned to minimize false positives and maximize alert relevance.
- Metrics:
- Reduction in false-positive alerts over time.
- Alerts correctly classified by priority and severity.
- Why it matters: Ensures internal teams can focus on real threats without alert fatigue.
3. KPI Achievement by Day 30 and Day 60
Tracking these KPIs demonstrates SOC effectiveness, operational improvement, and readiness for ongoing monitoring.
4. Operational Maturity and Compliance Readiness Metrics
- Operational Maturity:
- Full visibility into all critical assets.
- All dashboards are functional and provide actionable insights.
- Playbooks tested and internal teams trained.
- Compliance Readiness:
- Audit-ready reports aligned with regulatory standards (SOC2, ISO27001, HIPAA, etc.).
- Documentation of monitoring activities and incident handling procedures.
By monitoring these benchmarks, your organization can confidently measure progress during the first 60 days and ensure a smooth transition to a fully operational, optimized Managed SOC.
The first 60 days of a Managed SOC engagement are crucial for building a strong, resilient security posture. By following a structured onboarding process from pre-onboarding preparation and discovery, through tool deployment, detection tuning, and operational readiness your organization can achieve early visibility into threats, optimized alerting, and audit-ready compliance reporting. Key milestones, including integrated log sources, tuned detection rules, trained internal teams, and KPI dashboards, set the foundation for long-term security success.
CyberQuell’s Managed SOC services empower SMBs, IT teams, and executives to confidently monitor critical assets, respond to incidents, and maintain regulatory compliance without the burden of managing an in-house security team. With clear deliverables, performance benchmarks, and expert guidance, the first 60 days transform your security operations into a proactive, measurable, and reliable system.
CyberQuell delivers Managed SOC services that drive real results from day one. Request a quote today to see how our approach fits your organization’s security needs and business objectives.