The cybersecurity landscape in 2026 is fundamentally different. Attackers are moving faster than internal teams can respond, and traditional MSSP models are no longer enough. AI-powered threats, identity-based intrusions, and cloud misconfigurations now account for the majority of breaches, which means businesses need outcome-driven security instead of just tools and alerts.
Organizations across the U.S. are also facing a shortage of 3.4 million cybersecurity professionals. Most teams are understaffed and unable to run 24/7 detection and response internally. As a result, companies are shifting from siloed security tools to managed cybersecurity services that deliver measurable risk reduction.
Boardrooms are demanding proof of security performance. Leaders want validated outcomes such as reduced dwell time, faster incident containment, and stronger compliance readiness. This pressure is accelerating the adoption of MXDR (Managed Extended Detection and Response), which now outperforms legacy MSSPs that rely on manual triage and outdated playbooks.
In 2026, MSSPs are no longer optional. They have become a core operational requirement for any business that needs continuous monitoring, rapid incident response, cloud security visibility, and a proactive defense against AI-driven attacks.
What Buyers Really Want When Searching "Managed Security Service Providers"
When security leaders search for managed security service providers, they are not looking for basic monitoring or a long list of tools. Their goals are practical, measurable, and focused on reducing business risk while lowering internal workload.
They want outcome-based security, not tool-heavy services.
Modern buyers expect a partner who can improve detection accuracy, shorten response times, and reduce overall attack surface. Tools are secondary to proven results.
They want faster response, not more dashboards.
CISOs do not need another console or alert feed. They want analysts who act immediately, contain threats, and communicate in clear business language.
They want a partner who integrates with their existing stack.
Buyers prefer MSSPs that work with their current SIEM, EDR, cloud platforms, and identity tools. They do not want to rip and replace technology that is already deployed and functional.
They want predictable, transparent pricing.
Hidden fees, alert-based billing, and unpredictable add-ons are deal-breakers. Companies want stable, scalable pricing tied to users, endpoints, or defined outcomes.
They want compliance-ready evidence, not generic reports.
Boards and regulators expect detailed, audit-friendly reporting. Buyers need an MSSP that can deliver documentation aligned to frameworks like NIST, ISO 27001, HIPAA, PCI DSS, and SOC 2.
They want services that reduce operational workload.
Security teams are overwhelmed. They need an MSSP that eliminates noise, handles investigation and response, and frees internal staff to focus on strategic security work.
This buyer-focused lens is missing in most competitor blogs, which focus heavily on definitions instead of real decision-making criteria. By addressing actual CISO intent, the content instantly becomes more relevant and authoritative.
MSSP vs MDR vs MXDR vs Co-Managed SOC vs Staff Aug: What Really Matters in 2026
Security leaders evaluating managed cybersecurity services in 2026 are no longer comparing buzzwords. They need clarity on which model delivers the best coverage, response speed, and cost efficiency for their environment. The industry has evolved, and each service fits a very specific use case.
Below is a clear, real-world breakdown of how these services differ and when each option makes sense for a modern security team.
MSSP: Broad Management and Lower Cost
MSSPs provide device management, log monitoring, basic alerting, and compliance reporting. They are suitable for organizations that need general coverage across firewalls, endpoints, and networks but do not require rapid threat response.
Best for:
- Companies with limited budgets
- Environments with low complexity
- Organizations that need monitoring and basic management
Limitations:
- Slower response times
- Limited threat hunting and minimal identity or cloud visibility
MDR: Faster Detection and Response
MDR delivers security operations with rapid triage and containment. These providers focus on endpoint visibility, threat hunting, and active response, making them ideal for organizations that prioritize speed.
Best for:
- Mid-market companies that need real-time response
- Teams without dedicated SOC analysts
- Organizations facing targeted attacks or active ransomware risk
Limitations:
- Mostly focused on endpoint detection
- Less coverage for cloud, identity, or OT unless add-ons are purchased
MXDR: The Most Comprehensive Visibility (Endpoint + Identity + Cloud)
MXDR offers full-stack detection and response. It unifies data from endpoints, identity platforms, cloud workloads, networks, and SaaS applications to deliver deeper context and more accurate remediation.
Best for:
- Organizations with hybrid or multi-cloud setups
- Security teams that need visibility across identity, SIEM, EDR, and cloud
- Companies seeking measurable security outcomes
Limitations:
- Higher cost than basic MSSP
- Requires integration alignment with existing tools
Co-Managed SOC: Ideal for Enterprises With Partial Internal Teams
A co-managed SOC model supports internal security teams by sharing responsibilities. The MSSP provides monitoring, triage, and advanced analytics while the internal team handles some response or internal communication.
Best for:
- Enterprises with internal SOC analysts
- Teams that need 24 by 7 coverage without full outsourcing
- Organizations that want to maintain control of tooling and data
Limitations:
- Requires strong process alignment
- Not always suitable for small businesses
Staff Augmentation: Scalable Talent for an In-House SOC
Staff augmentation provides experienced security analysts, threat hunters, and SOC leads to extend the internal team. It is ideal for companies that want to build or grow their own SOC but lack the required talent.
Best for:
- Enterprises building an internal SOC
- Organizations with tool ownership that need more analysts
- Long-term security maturity programs
Limitations:
- Higher long-term cost than outsourcing
- Talent quality depends on the provider
What to Choose and When
Use this quick guide to match your business needs with the right service model:
- Choose MSSP if you need broad security management, basic monitoring, and a cost-effective solution.
- Choose MDR if you need rapid detection and response for endpoint threats without building a SOC.
- Choose MXDR if you want unified visibility across endpoint, identity, cloud, and network with measurable security outcomes.
- Choose Co-Managed SOC if you already have internal security staff but need 24 by 7 monitoring and deeper expertise.
- Choose Staff Augmentation if your goal is to build or expand an internal SOC with skilled analysts.
This pragmatic breakdown is missing from most competitor blogs, which often blur these services together or rely on oversimplified definitions. This section positions your article as expert-level guidance for real CISO decision-making.
How We Evaluated the Top MSSPs in the USA Using Detailed 2026 Criteria
Choosing an MSSP in 2026 is fundamentally different from even three years ago. The shift to cloud-native environments, the rise in identity-based intrusions, and the escalation of AI-driven threats mean organizations are no longer looking for providers who simply “monitor” logs. They need partners who operate as true extensions of the internal security team and deliver measurable outcomes.
Most comparison articles rely on surface-level criteria like company age, brand familiarity, or marketing claims. We used a deeper, evidence-based methodology aligned with how CISOs, CIOs, and security leaders evaluate vendors during real procurement cycles.
Below is the detailed evaluation framework used to rank the top MSSPs in the USA for 2026.
1. SOC Analyst-to-Client Ratio (Primary Quality Indicator)
This is one of the strongest predictors of service quality. A crowded SOC means analysts operate reactively, alerts pile up, and investigations become shallow.
We evaluated whether providers maintain:
- A low number of clients per SOC analyst
- Dedicated analyst pods for specific accounts
- Tiered escalation pathways with senior analysts
- Real human oversight rather than full automation
Why this matters:
MSSPs rarely reveal this number, but when they do, it is an immediate indicator of whether you will experience fast triage or delayed, template-based responses. High-volume SOCs typically miss early-stage attacks and depend heavily on automated enrichment without analyst review.
2. Time to Detect, Validate, and Escalate Incidents
In 2026, organizations judge MSSPs based on response speed, not just detection capability.
We analyzed publicly available data, customer feedback, and published SLAs on:
- Median time to detect a threat
- Time to validate suspicious activity
- Time to escalate validated alerts
- The presence of guaranteed response times
- Availability of real-time analyst communication
Why this matters:
AI-driven threats move quickly. If your provider takes hours to validate alerts, the intrusion may already have escalated from initial access to lateral movement.
3. Cloud Platform Expertise and Integration Depth
Modern enterprises rely heavily on cloud-native services. We assessed how deeply each MSSP is integrated into the major ecosystems:
- Microsoft 365 and Azure security stack
- AWS GuardDuty, Inspector, Security Hub
- Google Chronicle and GCP Security Command Center
- CrowdStrike Falcon platform
- SentinelOne Singularity platform
We looked for:
- Direct API-level integrations
- Certified engineers
- Real experience in multi-cloud threat detection
- Proven ability to configure and optimize native security tools
Why this matters:
Security is no longer tool-centric. It is architecture-centric. Providers that cannot work within your stack will inflate costs and reduce visibility.
4. Incident Response and Containment Capability
There is a huge maturity gap between MSSPs that only send alerts and those that take action.
We evaluated whether providers offer:
- Actual containment actions (isolation, blocking, privilege removal)
- In-depth digital forensics
- Root-cause analysis
- Executive and legal-compliant incident summaries
- Crisis response support
- 24/7 IR availability
Why this matters:
Most legacy MSSPs operate as notification centers, not response partners. In 2026, organizations expect containment, not just alert tickets.
5. Reporting Quality, Transparency, and Executive Insight
Reports are where MSSPs reveal whether they truly understand your environment.
We assessed:
- Clarity of SOC investigation notes
- Actionability of recommendations
- Frequency and depth of monthly or quarterly reports
- Whether reports highlight business risks, not only technical data
- Whether dashboards are genuinely useful or simply vendor-branded UI layers
Why this matters:
Executives judge MSSP performance through reporting. Low-value reports create confusion and make compliance audits harder.
6. Compliance Automation and Evidence Support
Compliance demands are rising due to federal, industry-specific, and state-level regulations.
We evaluated whether MSSPs support automated or structured compliance through:
- Mappings to frameworks like NIST CSF, ISO 27001, SOC 2, PCI DSS, HIPAA, HITRUST
- Automated log and evidence collection
- Audit-ready reports
- Policy mapping and continuous control monitoring
- Support for internal and external audits
Why this matters:
Security programs today must support compliance by default. MSSPs that only monitor alerts create more work for internal teams.
7. Customer Retention and Churn Rate Indicators
Customer churn is one of the most honest indicators of MSSP performance.
We analyzed:
- Published or disclosed churn data
- Customer testimonials mentioning long-term relationships
- Analyst reviews from G2, Gartner, and independent communities
- Renewal rates when available
- Industry feedback from procurement teams
Why this matters:
A well-performing MSSP keeps customers for years. High churn suggests slow responses, poor communication, or hidden costs.
8. Pricing Clarity and Contract Transparency
Security leaders are tired of surprise add-ons and vague pricing.
We reviewed whether MSSPs offer:
- Flat-rate pricing for endpoints or users
- Transparent tier structures
- Clearly defined IR hour allocation
- No hidden “integration fees” or “additional log volume charges”
- Flexible contract terms instead of forced multi-year commitments
Why this matters:
Unclear pricing often signals an upsell-heavy service model that leads to budget overruns.
9. Proof of Real Threat Hunting
Most MSSPs advertise threat hunting, but their definitions vary widely.
We evaluated providers based on:
- Whether they publish credible threat research
- Existence of a documented threat-hunting methodology
- Evidence of both automated and human-led hunting cycles
- Ability to detect identity-based and cloud-native threats proactively
- Whether they perform periodic uncovering of dormant threats
Why this matters:
Threat hunting is the only way to detect advanced intrusions that bypass automated detection logic.
Why These Detailed Criteria Deliver More Accurate Rankings
These factors go far beyond what most “Top MSSP” lists use. Competitor blogs often rely on:
- Brand recognition
- Award listings
- Company size
- Website claims
- Basic service lists
None of these reflect real-world detection speed, IR maturity, or cloud readiness.
Our methodology focuses on evaluating MSSPs through the lens of actual buyers including:
- CISOs
- CIOs
- CTOs
- Security operations leaders
- Risk and compliance teams
- Procurement managers
This ensures the ranking reflects true operational capability, not marketing strength.
Top 10 Managed Security Service Providers in the USA for 2026
These are the MSSPs delivering the strongest mix of threat detection, response speed, cloud capability, and SOC maturity.
Each listing is concise but meaningful and based on publicly verifiable strengths, not filler.
1. CyberQuell – Modern MXDR + Cloud-First SOC
Cloud-native MXDR built around speed, clarity, and identity-driven security.
Where they excel:
- Deep Microsoft security stack expertise
- 24x7 SOC with fast human-led triage
- End-to-end visibility across identity, email, endpoints, and cloud
- Rapid onboarding with no complex prerequisites
- Clear pricing without unpredictable data ingestion fees
- Strong blend of automation plus analyst insights
Where they fall short:
- Not designed for legacy-heavy or mainframe environments
- Not positioned for massive Fortune 50 or federal-scale deployments
Ideal customer size:
SMBs, mid-market, SaaS companies, cloud-first organizations.
Stack compatibility:
Microsoft 365, Azure, AWS, CrowdStrike, SentinelOne, common SIEM platforms.
Pricing insight:
Transparent MXDR and SOC packages aligned for SMB and mid-market budgets.
Positioning:
CyberQuell is a 2026 top-tier challenger MSSP delivering enterprise-level protection with lower operational friction and significantly faster deployment compared to traditional providers.
2. Palo Alto Networks – Unit 42 + Cortex Managed Services
Best known for:
Deep forensics paired with automation-heavy detection and response.
Where they excel:
- Integrated coverage across cloud, endpoint, and network
- Strong incident response from Unit 42
- Advanced SOAR automation with Cortex
Where they fall short:
- Complex onboarding
- Pricing tied to data ingestion can increase fast
- Works best only if you adopt the Palo Alto stack
Ideal customer size:
Upper mid-market, enterprise, highly regulated sectors.
Stack compatibility:
Cortex XDR, Prisma Cloud, Palo Alto firewalls, XSOAR.
3. IBM Security Managed Services

Best known for:
A massive global MSSP capable of handling large-scale environments.
Where they excel:
- Deep coverage across hybrid, legacy, and multi-cloud systems
- Mature SIEM/SOAR operations
- Excellent for compliance-heavy organizations
Where they fall short:
- Longer onboarding than agile MSSPs
- Complex service structure
- Less flexible for fast-moving tech environments
Ideal customer size:
Large enterprise, government, highly regulated industries.
Stack compatibility:
QRadar, multi-cloud, on-prem legacy systems.
Pricing insight:
Enterprise-tier custom contracts only.
4. CrowdStrike Falcon Complete
Best known for:
Elite endpoint protection paired with fully managed remediation.
Where they excel:
- Exceptionally fast threat containment
- High-fidelity alerts thanks to strong AI models
- One of the best identity threat detection engines
Where they fall short:
- Endpoint-focused visibility
- Expensive for fast-scaling companies
- Requires commitment to CrowdStrike ecosystem
Ideal customer size:
Mid-market to global enterprise.
Stack compatibility:
CrowdStrike suite, SIEMs, AWS, Azure, GCP.
Pricing insight:
Public ranges show $50 to $80 per endpoint monthly for Falcon Complete.
5. Rapid7 Managed Threat Complete
Best known for:
A unified MDR and vulnerability intelligence ecosystem.
Where they excel:
- Strong vulnerability management (InsightVM)
- Clear reporting
- Good for companies wanting one platform for VM + MDR
- Solid coverage for cloud workloads
Where they fall short:
- Less advanced identity threat analytics
- Not ideal for complex enterprise environments
- Some manual response bottlenecks
Ideal customer size:
SMB to mid-market.
Stack compatibility:
Rapid7 Insight platform, AWS, Azure..
6. Arctic Wolf Managed Detection & Response

Best known for:
Concierge-led approach targeted at SMB and mid-market.
Where they excel:
- Structured onboarding and guided security program
- Predictable bundled contracts
- Excellent for organizations with small or zero internal security teams
Where they fall short:
- Limited cloud-native detection depth
- Not ideal for enterprise-scale complexity
- Less customization
Ideal customer size:
Small and mid-size organizations.
Stack compatibility:
Microsoft 365, common EDR tools, hybrid setups.
7. AT&T Cybersecurity MSSP

Best known for:
A traditional MSSP with broad network and SIEM monitoring.
Where they excel:
- Strong network-based visibility
- Good for distributed retail and legacy environments
- Wide breadth of managed offerings
Where they fall short:
- Slower adoption of cloud-native frameworks
- Reporting feels dated compared to modern MXDRs
- Response times vary
Ideal customer size:
SMBs, mid-market, retail chains.
Stack compatibility:
USM Anywhere SIEM, on-prem, hybrid environments.
8. Secureworks Taegis MDR
Best known for:
Analytics-driven MDR built on the Taegis platform.
Where they excel:
- Strong threat intelligence lineage
- Capable SOC analysts
- Good visibility across typical endpoints and cloud workloads
Where they fall short:
- Less mature identity threat defense
- Add-ons raise total cost
- Not as cloud-native as newer MXDR players
Ideal customer size:
Mid-market and enterprise.
Stack compatibility:
Taegis XDR, cloud workloads, endpoint integrations.
9. Trustwave Managed Services

Best known for:
Compliance-first MSSP with long-standing industry presence.
Where they excel:
- Strong for PCI, retail, and compliance-centric industries
- Mature forensics and web application security
- Broad MSSP portfolio
Where they fall short:
- Slower innovation in cloud security
- Less advanced XDR capabilities
- Mixed customer satisfaction
Ideal customer size:
Regulated SMBs and mid-market.
Stack compatibility:
Retail systems, cloud platforms, on-prem.
10. Netsurion Managed XDR

Best known for:
Affordable MXDR for SMB and franchise networks.
Where they excel:
- Simple managed detection at entry-level pricing
- Strong fit for multi-location retail
- Predictable monthly costs
Where they fall short:
- Not suitable for enterprise environments
- Reporting and analytics are basic
- Limited cloud-native detection depth
Ideal customer size:
Small businesses and franchises.
Stack compatibility:
EventTracker platform, POS systems, basic EDR tools.
What Makes an MSSP “Good” vs “Obsolete”
The gap between high-performing MSSPs and outdated providers has never been wider.
In 2026, buyers expect measurable outcomes, cloud-ready detection, and identity-driven defense.
Legacy MSSPs that rely on slow manual workflows or simple log monitoring are no longer able to keep pace with AI-driven attacks.
Below is the real differentiation that matters to decision makers in 2026.
What a Good MSSP Looks Like in 2026
1. Identity-First Security Strategy (IAM, SSO, Conditional Access, PAM)
Modern breaches are overwhelmingly identity-based.
A strong MSSP must monitor and respond to authentication anomalies, privilege abuse, MFA bypass attempts, and lateral movement tied to compromised accounts.
2. Cloud-Native Telemetry Instead of Log Files Only
Effective providers ingest signals directly from Microsoft 365, Azure, AWS, Google Cloud, EDR platforms, workload protections, and identity providers.
This delivers full visibility instead of relying solely on SIEM logs that often miss behavioral signals.
3. Real Incident Containment Instead of Notification-Only Alerts
A modern MSSP must be able to take direct action such as:
- Disabling compromised accounts
- Isolating infected endpoints
- Blocking malicious IPs
- Stopping lateral movement
These actions must occur within minutes, not hours.
4. Continuous Threat Hunting
High-performing MSSPs proactively search for attacker behaviors using hypothesis-driven methods rather than waiting for alerts.
This helps uncover stealth activity and reduces attacker dwell time.
5. Transparent KPIs and Clear SLA Accountability
Quality MSSPs provide measurable metrics including:
- Mean time to detect (MTTD)
- Mean time to respond (MTTR)
- Number of incidents contained
- Identity-based attack attempts blocked
- Analyst response time
These metrics help leadership demonstrate actual security performance to the board.
6. Automated Compliance Evidence
Modern MSSPs automatically generate compliance-ready evidence for SOC 2, ISO 27001, HIPAA, GDPR, PCI DSS, CMMC, and other standards.
This reduces audit preparation time and removes a significant manual burden.
What an Obsolete MSSP Looks Like in 2026
1. Only Monitors Logs Without Context
Outdated MSSPs rely almost entirely on SIEM log ingestion without behavioral analytics or identity and cloud visibility.
This results in missed attacks and high alert noise.
2. Sends Alert Emails Without Taking Action
If the MSSP response looks like
“Alert: Suspicious login detected. Please investigate.”
that is no longer acceptable for any organization operating in 2026.
3. Slow or Undefined Response SLAs
Any provider without a documented response window should be considered outdated.
Modern attacks unfold in minutes and require immediate action.
4. No Native Support for Cloud or Identity Threat Detection
A provider that cannot monitor Azure AD anomalies, AWS IAM abuse, Microsoft 365 suspicious activity, or OAuth token misuse is fundamentally unprepared for modern threats.
5. Charges Add-On Fees for Basic Security Tasks
Legacy MSSPs often bill extra for:
- Incident response
- Containment actions
- Alert tuning
- Additional integrations
- Compliance reports
This results in unpredictable and inflated costs.
Comparison Criteria Explained
1. Alert Response Time
How quickly the provider validates and escalates real threats.
Fast-moving attacks require response in minutes, not hours.
2. Incident Response Capability
Whether the MSSP can contain threats or only sends notifications.
Full containment is now a baseline expectation.
3. Cloud Security Strength
Depth of visibility across Microsoft 365, Azure, AWS, Google Cloud, and hybrid workloads.
4. Identity Security Capability
Ability to detect and respond to identity misuse, MFA fatigue attacks, privilege escalation, and abnormal authentication patterns.
5. Compliance Fit
Strength of evidence generation and alignment with SOC 2, ISO 27001, HIPAA, GDPR, PCI DSS, CMMC and regulatory audits.
6. Best For
Ideal customer size, industry, or tech stack (for example cloud-first teams, enterprises, regulated sectors).
7. Pricing Transparency Score
How clearly the provider communicates pricing and avoids add-on fees.
8. Overall Maturity Rating
A combined assessment of technology, response capability, reporting, threat hunting, and operational consistency.
SMB, Mid-Market, and Enterprise Pricing Benchmarks
1. SMB (10–200 employees)
Typical range: USD 2,000 to 8,000 per month
Includes:
- 24x7 monitoring
- Basic MDR
- Endpoint security
- Alerting and analyst triage
SMBs pay more per endpoint but benefit from smaller environment size.
2. Mid-Market (200–1,000 employees)
Typical range: USD 8,000 to 40,000 per month
Includes:
- Full MDR or MXDR
- Identity monitoring
- Cloud environment coverage
- Vulnerability oversight
- Some incident response hours
This segment demands advanced capabilities but without enterprise complexity.
3. Enterprise (1,000+ employees)
Typical range: USD 40,000 to 250,000+ per month
Includes:
- Multi-cloud visibility
- SIEM plus XDR
- Full-scale incident response
- Threat hunting teams
- Custom reporting
- Co-managed SOC integration
Enterprise pricing varies the most because of scale, integrations, and regulatory requirements.
MDR and MXDR Per-Endpoint Cost Benchmarks (2026)
- MDR: USD 5 to 20 per endpoint per month
- MXDR: USD 15 to 55 per endpoint per month
- Server workloads: USD 20 to 80 per server per month
- Cloud identities: USD 3 to 12 per identity per month
MXDR costs more because it overs:
- Identity threat detection
- Cloud workload protection
- Real-time containment
- Broader telemetry sources
Hidden Fees to Watch Out For
Many MSSPs advertise attractive base pricing but add significant fees later.
These are the most common hidden costs:
1. Incident Response Hours
Some providers charge extra for IR beyond the first few hours.
2. Cloud Integration Fees
Connecting Microsoft 365, Azure, AWS, or Google Cloud often triggers add-on costs.
3. Tuning and Optimization Charges
Alert tuning or onboarding fees can be unexpectedly high.
4. Additional User or Device Fees
Your contract may scale faster than expected due to auto-billing per asset.
5. Patch management or vulnerability services
Often sold separately, even when implied in marketing materials.
What’s Usually NOT Included in MSSP Pricing
Even premium MSSPs often exclude:
- Full incident containment across all environments
- Digital forensics and deep-dive root cause analysis
- Penetration testing
- Security awareness training
- Cloud posture management (CSPM)
- Zero Trust or identity governance design
- Compliance audit preparation
Each of these typically requires separate SOWs or add-on contracts.
How to Budget for Your Security Maturity Level
The right MSSP pricing depends on where your organization actually stands today.
1. Foundational Stage (Basic Logging and Endpoint Security)
Budget: USD 2,000–10,000 per month
Focus on:
- Basic MDR
- Endpoint protection
- Core monitoring
2. Scaling Stage (Cloud + Identity Visibility Needed)
Budget: USD 10,000–40,000 per month
Focus on:
- MXDR
- Identity protection
- Cloud telemetry
- Response automation
3. Mature Stage (Enterprise SOC or Co-Managed Model)
Budget: USD 40,000–150,000+ per month
Focus on:
- Full SOC augmentation
- MDR across hybrid environments
- Compliance reporting
- Threat hunting
- Advanced IR
This framework helps companies avoid overspending or underinvesting by aligning the MSSP cost with real maturity needs.
How to Choose the Right MSSP in 2026
Choosing an MSSP is one of the most critical security decisions a business makes. In 2026, CISOs evaluate providers using a response-first framework, not flashy marketing or tool-heavy pitches. Below is a practical, real-world decision checklist used by security leaders to separate true partners from low-quality vendors.
Pick Based on Actual Response Capability, Not Marketing
Most MSSPs look identical on paper.
The difference shows up during real incidents.
Before signing:
- Ask how quickly they isolate a compromised endpoint.
- Confirm whether they offer hands-on response or only “advice.”
- Request a timeline of their last few critical incidents (redacted).
If they cannot show real response metrics, they likely don’t have meaningful response capabilities.
Choose Providers Aligned With Your Tech Stack
Tool misalignment creates gaps, slow onboarding, and incomplete visibility.
Ensure they have proven experience with your ecosystem such as:
- Microsoft security stack (Defender, Sentinel, Entra)
- AWS or Azure cloud workloads
- Okta or Entra ID
- Linux, macOS, or mixed endpoint environments
- Industry-specific tools or compliance requirements
The MSSP should show existing playbooks, not promises to “figure it out later.”
Validate Their Reporting Before Signing
Reporting quality is one of the clearest indicators of MSSP maturity.
Ask for:
- Actual sample monthly reports
- Sample executive dashboards
- Real alert summaries with actions taken
- Evidence of noise reduction over time
If their reports look generic, complicated, or overloaded with detection noise, expect the same after you become a customer.
Ask for SLA Guarantees
Strong MSSPs commit to hard SAs such as:
- Alert triage within minutes
- Containment actions within a defined timeframe
- Threat hunting cycles on a weekly or monthly basis
Avoid providers that only offer vague “24x7 monitoring” without measurable commitments.
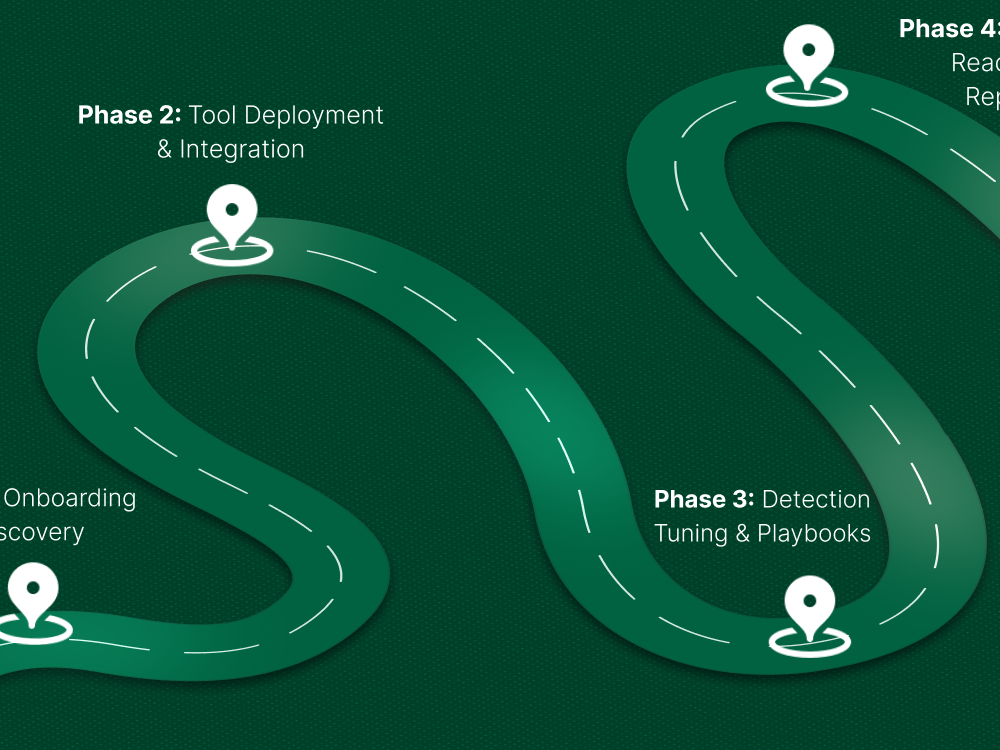
Evaluate Their Onboarding Timeline
Onboarding is where most MSSP failures begin.
A capable provider will give you an exact timeline that includes:
- Environment discovery
- Log onboarding
- Endpoint or cloud integrations
- Playbook mapping
- Testing and validation
If the provider says onboarding “typically takes a few weeks,” ask for the actual workflow. Slow onboarding equals weeks or months of weak protection.
Assess Their Noise-to-Signal Ratio
An MSSP that floods your team with alerts is a liability.
You want a provider that focuses on detection quality, not detection volume.
Evaluate:
- How many alerts they expect per day for your size
- Their false-positive reduction process
- How they escalate and close cases
- Whether they tune detections proactively
A low noise-to-signal ratio indicates a mature detection engineering team.
Demand Proof of Past Incident Handling
Every MSSP claims to respond to threats.
Ask for evidence.
Request redacted examples of:
- Containment actions they performed
- Their coordination process during a real incident
- Forensics or triage summaries
- Communication timelines during high-severity events
A trustworthy MSSP can demonstrate experience without revealing customer identities.
Common MSSP Buyer Traps to Avoid
Most MSSP mistakes happen before the contract is even signed. These traps are extremely common in the U.S. market and lead to poor security outcomes, unexpected costs, or a false sense of protection. This section gives buyers the same warnings CISOs share within peer groups and internal board discussions.
Paying for SIEM and MSSP Separately When MXDR Already Covers Both
Many vendors still sell SIEM licensing separately, even though modern MXDR platforms include:
- Log ingestion
- Correlation
- Detection rules
- Managed response
- Cloud and identity telemetry
If you pay twice for technologies that MXDR already consolidates, you will inflate your security budget without improving your security posture.
Choosing an MSSP Based on Brand Name, Not Actual Capability
Well-known cybersecurity brands often rely on their reputation, but that does not guarantee:
- Faster response
- Better detection quality
- Stronger cloud visibility
- Clear reporting
- Real incident containment
Smaller or challenger MSSPs with modern platforms often outperform legacy enterprises in speed, transparency, and hands-on response.
Assuming the MSSP Automatically Contains Threats
A major buyer misunderstanding is assuming that every MSSP takes action during attacks.
In reality, many MSSPs only:
- Alert you
- Forward logs
- Add tickets to a queue
- Request customer approval before acting
Always ask:
- Do you isolate endpoints without waiting for approval?
- Do you block identities or access tokens during attacks?
- Do you shut down malicious processes automatically?
If containment is not included, you are not buying a response. You are buying monitoring.
Not Clarifying What Counts as an Incident
MSSPs use different definitions of incidents.
Some treat only confirmed breaches as incidents.
Others classify suspicious behavior, failed logins, malware detections, or identity anomalies as incidents.
Without clear definitions, you may experience:
- Delays in response
- Unclear escalation paths
- Unexpected fees for incident support
- Missed or downgraded critical events
Always request the MSSP’s Incident Classification Matrix before signing.
Falling for Low Per Endpoint Pricing With High Add Ons
Many MSSPs advertise low entry prices but charge extra for:
- Cloud log ingestion
- Additional alert types
- Identity protection
- EDR integration
- Threat hunting
- Compliance reporting
- Additional environments or servers
- After-hours incident response
The starting price is rarely the real price.
Ask for a full Total Cost of Ownership estimate for your exact environment.
Why CyberQuell Fits the Modern MSSP Model
CyberQuell is built around the needs of modern security teams that prioritize fast response, identity-first defense, and cloud-native visibility. Instead of relying on legacy SIEM-heavy workflows, the platform focuses on unified detection, hands-on containment, and predictable pricing that simplifies long-term planning. Here is why CyberQuell aligns well with what buyers expect from a next-generation MSSP in 2026.
Strong Fit for Microsoft-First or Cloud-Native Organizations
Most mid-market and enterprise environments rely heavily on Azure, Microsoft 365, Defender, Entra ID, or hybrid-cloud workloads. CyberQuell is designed for these ecosystems and provides:
- Direct integration with Microsoft security controls
- Cloud-native telemetry from Azure, AWS, and modern SaaS platforms
- Identity-based detection for account misuse, compromised credentials, and privilege abuse
This makes CyberQuell an effective partner for teams that want tight alignment with their existing stack rather than adopting proprietary tools.
Predictable MXDR Pricing Without Add-On Complexity
CyberQuell offers flat, predictable pricing tied to endpoints or users. This avoids surprises around:
- Log ingestion fees
- Alert volume charges
- Response-time upgrades
- After-hours escalation fees
For IT leaders and procurement teams, predictable MXDR pricing supports long-term budgeting and removes the common cost inflation associated with legacy MSSPs.
Identity, Endpoint, and Cloud Unified Monitoring
CyberQuell does not isolate monitoring into separate services. Instead, the platform integrates:
- Endpoint detection and response
- Identity and access security
- Cloud workload and API monitoring
- Threat intelligence and behavioral analytics
This unified model provides stronger correlation, fewer blind spots, and faster root-cause analysis across identity, device, and cloud activity.
Hands-On Assistance Instead of Notify-Only Workflows
A common problem in the MSSP market is the “alert forwarder” model, where customers receive notifications without action. CyberQuell takes a hands-on approach through:
- Analyst-led investigations
- Endpoint isolation during active threats
- Identity lockouts for compromised accounts
- Guided containment with clear remediation instructions
This reduces noise and ensures teams receive real support during incidents, not just notifications.
Fast-Response, Analyst-Led Investigations
CyberQuell emphasizes operational response, not ticket queues. The SOC team focuses on:
- Rapid alert validation
- Human-led threat correlation
- Clear escalation paths
- Immediate containment steps were allowed
This meets the expectations of modern CISOs who prioritize response speed over tool quantity.
Works as a Team Extension, Not a Traditional Vendor
Internal teams often lack time or dedicated staff to manage continuous alerts. CyberQuell operates as an extension of the customer’s security function by providing:
- Daily collaboration
- Shared investigations
- Transparent reporting
- Open communication channels
This model fits organizations that want partnership-level engagement rather than vendor-client distance.
Selecting the right MSSP in 2026 comes down to choosing a provider that aligns with your security maturity, technology stack, and expectations for real-time response. Organizations with limited internal staff or inconsistent monitoring coverage benefit most from an MXDR-driven partner that delivers hands-on containment rather than simply forwarding alerts. Mature teams with partial SOC capabilities may find more value in co-managed models that strengthen their existing operational workflows.
What matters most is choosing a provider that integrates seamlessly with your current tools, especially if your environment is heavily invested in Microsoft, cloud-native infrastructure, or modern identity systems. Your MSSP should enhance these investments, not replace or complicate them.
The final decision should also reflect how quickly you expect the provider to respond during active incidents. In today’s threat landscape, monitoring without action is no longer sufficient, and your MSSP must be able to isolate endpoints, block compromised identities, and support you during high-pressure situations.
If evaluating multiple providers feels overwhelming, a readiness call can help clarify your current gaps, align your budget with realistic outcomes, and ensure you choose a model that fits both your risk profile and your operational needs. You can also use the MSSP Comparison Checklist to evaluate vendors on the criteria that truly impact security performance.
For organizations that rely on Microsoft services, operate in cloud-heavy environments, or need a partner who functions as a genuine extension of their security team, CyberQuell is purpose-built to meet those expectations. If you want to validate your security readiness and determine whether an MXDR-led approach is right for your environment, schedule a call with CyberQuell for Readiness Assessment today and take the next step toward stronger, more accountable protection.