If you're working in or running a security operations team, you've probably said this more than once:
“We don’t need more alerts, we need more time.”
Every day, SOCs are buried under a mountain of notifications, phishing emails, suspicious logins, vulnerability scans, endpoint anomalies and there just aren’t enough people to go around. Even experienced analysts are spending their time manually doing things that, frankly, a machine could probably handle better and faster.
That constant grind leads to burnout. Threats slip through the cracks. And response times? They suffer.
This is where SOAR comes in. And no it’s not some silver bullet or overhyped buzzword. At its core, SOAR is just a practical way to help security teams get their time back by automating the stuff that doesn’t need human hands on it 24/7.
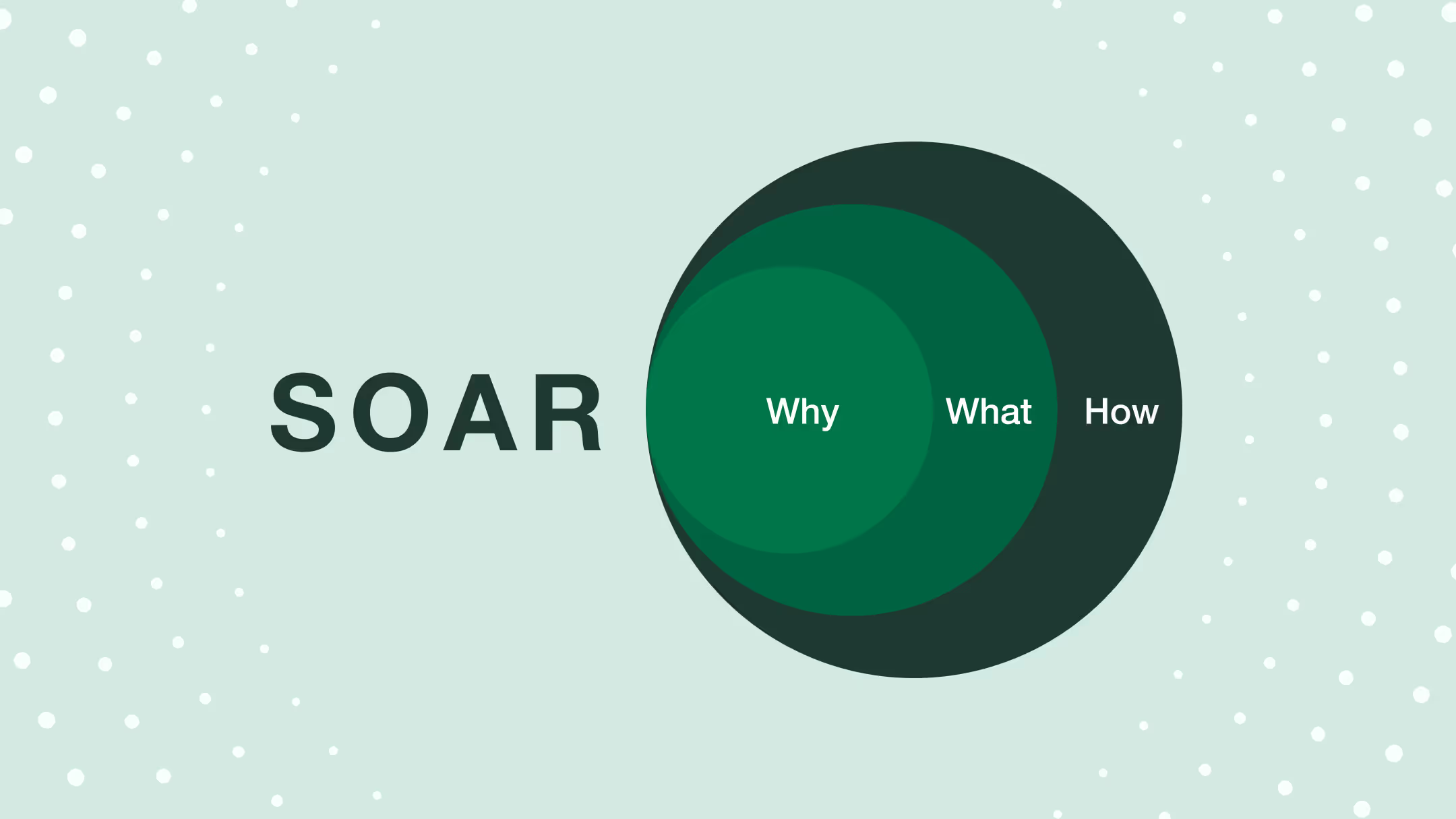
What Is SOAR? (Without the Marketing Lingo)
Let’s keep this simple.
SOAR stands for:
Security Orchestration, Automation, and Response.
That’s a mouthful, so let’s unpack what it actually means in practice:
- Orchestration is about connecting the tools you already use: your SIEM, EDR, firewalls, threat intel feeds, ticketing systems and letting them talk to each other in a coordinated way.
- Automation means handling repetitive security tasks (like triaging alerts or isolating a device) without needing a human to manually step in every time.
- Response is about standardizing and speeding up how you deal with incidents, so your team isn’t reinventing the wheel for every phishing email or malware alert.
In short: SOAR helps your tools work together, and helps your team work smarter.
What Does SOAR Actually Do in a Security Team’s Day-to-Day?
Here’s what a SOAR platform can take off your team’s plate:
- Auto-triaging low-level alerts from your SIEM
- Pulling in threat intel to enrich an alert with context
- Automatically opening a ticket (or closing it if it’s a false alarm)
- Isolating a compromised endpoint through your EDR
- Sending a Slack message or email to the right person instantly
Instead of your analysts juggling a dozen consoles and clicking through steps they’ve done a hundred times, SOAR runs those workflows in the background.
Where Does SOAR Fit in Your Stack?
It doesn’t replace your SIEM. It doesn’t compete with your EDR.
SOAR works with them as the glue that connects everything and adds decision logic on top.
Here’s a quick way to think about it:
So instead of treating each tool as a silo, SOAR brings them together to act like one well-coordinated system.
Why SOAR Matters Right Now
Let’s be honest, most security teams aren’t short on tools.
They’re short on time. And people.
Today’s SOCs are overwhelmed. Alerts pile up faster than they can be reviewed. Analysts spend their days on repetitive triage work. Critical threats get delayed because everyone’s stuck clearing out the noise.
That’s the real issue SOAR is designed to fix.
It’s not about replacing analysts with automation.
It’s about giving them the breathing room to do what they’re best at: solving problems, investigating real threats, and improving security, not clicking through endless queues of low-priority alerts.
The Impact of “Alert Overload”
Here’s what security teams deal with every day:
- Too many alerts, most of them low-value
- Manual phishing triage, even for common attacks
- Slow incident response because everything needs human hands
- Burnout from constantly being reactive instead of proactive
And the bigger the environment, the worse it gets. One missed alert could mean a breach but there’s no way to review them all without help.
How SOAR Changes the Game
SOAR doesn’t make these problems disappear but it does make them manageable.
By automating what doesn’t need human judgment, teams can:
- Reduce time-to-response (MTTR) by 60% or more
- Auto-resolve 50–70% of phishing emails
- Handle 2x–3x more alerts per analyst
- Free up time for threat hunting, playbook tuning, or actual incident response
That kind of shift doesn’t just help the numbers, it helps morale. Your team goes from constantly firefighting to actually running a system that works.
What SOAR Platforms Actually Do (Plain and Practical)
Let’s get into the real day-to-day of SOAR, not the shiny diagrams or product brochures, but what it actually does when it's in use by a security team like yours.
At its core, a SOAR platform connects your security tools, automates repeatable work, and helps your team act faster with more confidence and less manual effort.
Here’s how it does that:
1. Connects Your Security Stack
SOAR acts as the central nervous system for your tools. It pulls in alerts, context, and data from places like:
- Your SIEM (Splunk, Sentinel, etc.)
- EDR platforms (CrowdStrike, SentinelOne, etc.)
- Firewalls and network gear
- Threat intelligence feeds (open-source, commercial, or internal)
- Ticketing systems (Jira, ServiceNow)
- Messaging tools (Slack, email, Teams)
Instead of jumping between consoles and copying data from one system to another, SOAR puts everything in one flow and automates the handoffs.
2. Runs Automated Workflows (a.k.a. Playbooks)
Playbooks are where the real magic happens.
These are prebuilt or custom workflows that tell SOAR what to do when something happens like:
- If a phishing email is reported → scan it → check sender reputation → sandbox attachment → update ticket → notify user
- If a malware alert comes in from your EDR → isolate the device → enrich with asset data → assign to IR lead
Once a playbook is built and tested, it runs the same way every time fast, consistent, and without human delay.
3. Enriches Alerts with Context
One alert from a SIEM isn’t always enough to know what’s going on.
SOAR helps by automatically pulling in useful context:
- Is this IP linked to known threats?
- Has this user triggered other alerts recently?
- Is the affected endpoint exposed to the internet?
- Has this exact incident happened before?
That way, your analysts don’t have to dig for the info that is already there.
4. Triggers Actions, Automatically
Once SOAR has the data and context, it can take action either automatically or with human sign-off.
Some examples:
- Open or close a ticket
- Isolate a machine from the network
- Block a sender at the email gateway
- Notify a channel in Slack or Microsoft Teams
- Update compliance logs or dashboards
The goal isn’t to remove people, it's to speed things up where you can, and make life easier where you can’t.
5. Provides Dashboards and Logs for Tracking
Good SOAR platforms also help you stay accountable.
You get:
- Logs of what was automated (and when)
- Visibility into playbook performance
- Metrics like: time saved, incidents resolved, steps skipped
- Easy reporting for compliance or audits
That means you’re not just faster, you're more measurable, too.
Top Use Cases (Where SOAR Actually Saves Time)
If you’re still wondering what SOAR really does once it’s up and running this is it. Below are some of the most common (and painful) workflows where SOAR can give your security team hours back every week.
No theory. Just real problems solved with simple, automated workflows.
1. Phishing Triage & Remediation
Before SOAR
A user reports a suspicious email. An analyst manually checks the sender, looks up IPs, downloads attachments to sandbox them, checks for links, pulls logs, opens a ticket… all while five more alerts stack up.
After SOAR
- Email is scanned automatically
- Header info and attachments are analyzed
- Reputation checked via threat intel feeds
- If clean → auto-close
- If malicious → isolate user, create ticket, notify IR
Time saved per email: Up to 30–45 minutes
Resource: Phishing Response Playbook Example – Palo Alto Cortex XSOAR
2. Malware Alert to Endpoint Isolation
Before SOAR
EDR detects suspicious behavior. The analyst is notified via SIEM, then has to switch tools, investigate, contact IT to isolate the host, and create a ticket.
After SOAR
- EDR alert triggers a SOAR playbook
- SOAR pulls context (host name, user, recent activity)
- If high-risk → automatically isolates the endpoint
- Ticket is opened with all logs + context already included
Time saved: 60+ minutes per high-severity malware alert
Reduced dwell time: Threats contained in minutes, not hours
Resource: CrowdStrike + SOAR Integration Overview
3. SIEM Alert Enrichment + Auto-Prioritization
Before SOAR
SIEM triggers a generic alert with no context. The analyst has to manually pull asset info, threat intel, and user behavior logs before even deciding if it’s important.
After SOAR
- SIEM alert lands in SOAR
- Playbook enriches it with asset data, user info, threat intel
- Assigns a risk score
- If low-risk → auto-close
- If medium/high → escalates to the right analyst with all context
Result:
- Fewer false positives
- Priority alerts get attention faster
- Less analyst fatigue from "just-in-case" investigations
Resource: Splunk Phantom Use Case Library
4. Insider Threat Investigation
Before SOAR
Suspicious behavior from an internal user, say downloading large files at odd hours. An analyst has to cross-reference access logs, user behavior, emails, endpoints, and more.
After SOAR
- Behavior analytics triggers a SOAR workflow
- SOAR pulls recent access logs, file download records, login activity
- Compares to baselines or past incidents
- Flags risk, creates case with evidence, notifies IR
Result:
- Faster insider risk validation
- Analysts get full picture without jumping through 5 tools
Resource: MITRE Insider Threat Use Case Framework
How SOAR Works With SIEM (Not Instead of It)
Let’s clear something up SOAR doesn’t replace your SIEM.
In fact, SOAR isn’t much use without one.
Your SIEM is still the backbone. It’s the tool that ingests logs, correlates data, and flags suspicious behavior. But here’s the catch:
SIEMs are great at telling you something’s wrong not so great at deciding what to do next.
That’s where SOAR comes in.
SIEM + SOAR = Smarter, Faster Incident Handling
Think of it this way:
Let’s say your SIEM detects a brute force login attempt.
Here’s how it would play out with SOAR in the mix:
Example Workflow: From SIEM Alert to Action
- SIEM raises an alert about multiple failed logins from a foreign IP
- SOAR picks up the alert, launches a playbook
- It enriches the alert using threat intel (Is the IP on a known blacklist?)
- It pulls user context from Active Directory or identity platforms
- Based on logic, it might:
- Auto-lock the account
- Open a ticket in Jira or ServiceNow
- Send a Slack/Teams alert to the SOC
- Escalate the case to Tier 2 with all context attached
- Auto-lock the account
No tab-hopping. No redundant steps. Just decisions made fast, repeatable, and logged.
Common SIEM + SOAR Stacks You’ll See Out There
- Splunk + Phantom (SOAR)
Still one of the most widely used setups. Splunk handles heavy-duty log collection and alerting; Phantom automates what happens next. - Microsoft Sentinel + Logic Apps
For Azure-centric orgs, this pairing allows full-stack integration across cloud, identity, and SecOps tools. - IBM QRadar + Resilient SOAR
Big in regulated industries. QRadar feeds enriched alerts into Resilient, which can act or escalate based on playbooks. - Elastic SIEM + Cortex XSOAR
A lighter-weight but growing stack, especially for fast-moving teams.
The point? You don’t need to replace your SIEM to get started with SOAR.
You just need to connect them and start small with a few high-impact workflows.
SOAR + EDR: Containment Without Waiting
So you’ve got a strong EDR in place CrowdStrike, SentinelOne, Defender for Endpoint, take your pick.
It detects malware, flags suspicious behavior, and provides visibility on what’s happening at the endpoint level.
But here’s the problem: detection alone isn’t enough.
When malware hits an endpoint, someone still needs to:
- Investigate what triggered the alert
- Decide whether the device should be isolated
- Notify the right people
- Update the IR ticket
- Track it all for compliance or reporting
That takes time and in many cases, by the time someone acts, the damage is already done.
This is where SOAR steps in.
How SOAR Supercharges Your EDR
With SOAR in the mix, those manual steps become part of an automated playbook.
Here’s how it plays out:
- EDR flags malware activity on a user’s device
- SOAR immediately picks up the alert and checks:
- What process was flagged?
- Who’s logged into the machine?
- Is this device sensitive (e.g., exec laptop or finance system)?
- What process was flagged?
- If the playbook criteria match, SOAR can:
- Isolate the device from the network
- Notify IR or the SOC lead
- Open a ticket in Jira/ServiceNow with all the enriched context
- Push a summary to Slack or Teams for visibility
- Isolate the device from the network
All of this happens in seconds, not hours.
Why It Matters
- Reduced dwell time: The faster you isolate, the less risk of spread
- Less analyst lag: Your team isn’t stuck waiting for alerts to escalate
- More consistent response: You don’t rely on someone manually following a checklist
A Word of Caution: Don’t Skip the Human Testing
While this sounds powerful (and it is), automating response without context can backfire.
You don’t want to isolate a machine every time there's a false positive. That’s why it’s smart to:
- Start with playbooks that require human approval before action
- Use a staging environment to test automations before going live
- Set clear risk thresholds so only high-confidence detections trigger full response
Think of SOAR as your assistant, not your replacement. It still needs guardrails especially when it comes to decisions that could impact live systems or users.
The SOAR Playbook Lifecycle (Design → Test → Improve)
If the idea of building automation workflows sounds overwhelming you're not alone.
But here’s the thing: you don’t have to build everything at once. Most successful SOAR rollouts start small and evolve over time.
Think of playbooks as repeatable checklists your SOAR platform can run for you.
They follow the same logic your analysts would just faster, and without dropping the ball when things get busy.
Here’s how the lifecycle of a SOAR playbook typically works:
1. Spot the Repetitive Stuff
Start by looking at what your team does every day that’s:
- Manual
- Repetitive
- Slowing things down
For most SOCs, this usually includes:
- Phishing investigations
- Basic malware alert handling
- Auto-ticketing for known issues
- Alert enrichment steps (looking up IPs, user info, etc.)
These are great candidates for your first playbook.
2. Design the Workflow (Keep It Simple)
Now, sketch out the steps your analyst normally follows. Literally pen and paper is fine.
Example:
- Alert comes in from SIEM
- Check if it’s a known IP
- Pull asset and user info
- Open a ticket if it meets criteria
- Notify IR via Slack
This “if-this-then-that” logic becomes the blueprint for your SOAR playbook.
Most platforms offer visual drag-and-drop builders, so you don’t need to code.
3. Test in a Safe Environment
Before you automate anything live, test it.
Use a sandbox or a low-risk alert type. Make sure:
- The logic works
- The right actions are taken
- Nothing breaks or disrupts other systems
In early stages, it’s smart to require human approval before SOAR acts. That way, your team stays in control while the automation proves itself.
4. Measure What Matters
Once it’s live, don’t just “set and forget.” Track what’s working and what’s not.
Metrics to watch:
- MTTR (Mean Time to Respond) did it drop?
- Analyst workload is the team less buried in alerts?
- Manual intervention rate: how often does SOAR need a human to step in?
- Accuracy is the automation doing what you expect?
This feedback loop helps you fine-tune over time.
5. Optimize and Document
After a few cycles, tweak the playbook:
- Remove steps that aren’t needed
- Add new checks for better accuracy
- Automate more once you trust the logic
Then, document it:
- What it does
- When it runs
- Who owns it
- What success looks like
Good documentation ensures playbooks are manageable and survivable if your team changes.
Best Practices: Getting the Most from SOAR Without Burning Out Your Team
Here’s the honest truth: the fastest way to fail with SOAR is trying to do too much, too fast.
It’s easy to get excited about automation. But when you overcomplicate playbooks, skip testing, or don’t get buy-in from the right people, SOAR turns into another tool your team quietly avoids.
Here’s how to roll it out the right way without burning out your analysts or breaking your stack.
1. Start Small (But Start)
Pick one or two high-friction tasks that your team is constantly repeating:
- Phishing triage
- Alert enrichment
- Auto-ticketing for known issues
Get those working first. Build trust in the system. Then expand from there.
2. Use KPIs That Actually Matter
Set clear goals so you can measure success early on.
Some useful starting metrics:
- Percentage of alerts auto-triaged
- Reduction in MTTR
- Time saved per playbook run
- % reduction in manual effort for a specific use case (e.g., phishing)
This gives your team something real to point to and helps prove the value to leadership.
3. Keep Playbooks Simple at First
You don’t need 20 branches and nested decision trees to make an impact.
In fact, the best early playbooks look more like this:
- Alert → Enrich → Evaluate → Take 1 action → Document
Simple playbooks are easier to build, easier to test, and easier to trust.
4. Bring in the Right People Early
SOAR doesn’t just affect the SOC it touches everything from incident response to compliance to IT operations.
Loop in stakeholders early:
- IR teams to define actions and thresholds
- GRC teams to handle audit and documentation requirements
- IT ops to support endpoint actions or ticketing flows
The earlier you align, the smoother your rollout.
5. Assign Ownership (Yes, Someone Has to Own It)
Playbooks aren’t “set it and forget it.” They’ll need updates as your environment changes.
Make sure someone is responsible for:
- Reviewing what’s working (and what’s not)
- Updating workflows when tools or processes change
- Keeping documentation current
- Training new analysts on how automation fits in
Without ownership, SOAR efforts tend to fizzle.
Don’t Forget the Threat Intel
It’s easy to focus on automation and workflows when setting up SOAR but there’s one critical piece that often gets overlooked:
What’s feeding the decisions your playbooks are making?
SOAR is only as smart as the data it runs on.
If that data is shallow, outdated, or lacks context your automation will be too.
That’s where threat intelligence comes in.
Why Threat Intel Matters in SOAR
Threat intel isn’t just something you review in dashboards. When integrated with SOAR, it becomes part of the decision-making process.
For example:
- An alert from your SIEM shows a login attempt from a new IP
- On its own, it’s suspicious but not urgent
- SOAR enriches it with threat intel and finds that the IP is tied to a known ransomware group
- Now it’s high-priority and gets escalated immediately
That’s a smarter, faster response and it happens automatically.
What to Integrate
Good SOAR platforms let you connect a mix of:
- Free intel feeds like AbuseIPDB, AlienVault OTX, or open CVE databases
- Paid threat intel providers like Recorded Future, Mandiant, Flashpoint, etc.
- Internal sources, like previous IR reports, known bad domains, or blocked IOCs from past incidents
This blended intel helps your SOAR engine:
- Auto-prioritize alerts based on real-world threat relevance
- Enrich tickets with context (e.g., “This IP is part of an active botnet”)
- Filter out noise so analysts focus on what matters most
Example in Action
Let’s say your EDR flags suspicious PowerShell activity.
Without intel, it’s just another alert.
But with threat intel enrichment:
- SOAR checks the hash or domain involved
- Finds it listed in a current ransomware campaign
- Escalates it immediately, isolates the host, and notifies IR
- Adds CVE or TTP details directly into the case for faster triage
Now that’s automation with teeth.
People, Process & Change Management: The Hidden Challenge
Let’s talk about something that rarely gets mentioned in SOAR vendor pitches —
your team’s reaction.
Because here’s the truth:
Even if SOAR works perfectly from a technical standpoint, it can still fail if your people don’t trust it.
And it’s not hard to understand why.
“Wait… Is This Replacing My Job?”
That’s often the first thought.
If you’re a SOC analyst, and a new tool shows up that promises to automate all the things you do every day it’s natural to feel a little nervous.
But SOAR doesn’t replace people. It replaces the boring.
- Clicking through 20 tabs to investigate a phishing email
- Copy-pasting IPs between tools
- Manually opening tickets for things you’ve seen a hundred times
Those are the things SOAR is built to eliminate so your analysts can focus on thinking, investigating, and actually improving security posture.
How to Roll It Out Without Losing Your Team
Here’s what makes the difference:
1. Start with a Guided Rollout
Pick a few non-threatening, low-risk use cases (like alert enrichment or auto-ticketing). Involve analysts in designing the playbook, so they feel ownership not surprise.
2. Be Transparent with KPIs
Share what you're measuring and why. For example:
“We want to reduce phishing triage time by 60%, so you can spend more time on threat hunting.”
When people understand the why, resistance goes down.
3. Let Them Test It
Give your team access to a sandbox. Let them run the playbooks, break them, see how they behave. When they see how the automation works, it builds trust.
4. Upskill Alongside Automation
SOAR creates new opportunities for analysts, not fewer.
Playbook design, workflow logic, tool integration these are all skills that help junior analysts grow into senior ones. Treat SOAR rollout as a learning opportunity, not just a tech deployment.
SOAR Isn’t Just for Enterprises Anymore
For a long time, SOAR had a reputation:
Too complex. Too expensive. Too enterprise.
And to be fair, that used to be true. The early platforms were heavyweight, on-prem, and needed dedicated engineers just to get started.
But that’s changed.
Modern SOAR Is Lighter, Faster, and Cloud-Ready
Today’s SOAR tools are built to be more flexible:
- Cloud-native platforms that don’t require weeks of setup
- Drag-and-drop playbook builders that don’t need a scripting background
- Prebuilt integrations for common tools like CrowdStrike, Sentinel, Jira, and Slack
- Scalable pricing based on use, not enterprise license size
That makes it a lot more realistic for mid-sized teams to get the benefits without the baggage.
MSSPs Use SOAR to Scale Efficiently
Managed Security Service Providers (MSSPs) have quietly become some of the most advanced SOAR users and for good reason.
When you're managing alerts across 10, 20, or 50 clients, you don’t have time for manual triage every time an endpoint pings. SOAR helps MSSPs:
- Normalize workflows across client environments
- Automate repeatable tasks
- Deliver consistent incident handling
- Prove value through metrics and audit trails
You don’t need a massive in-house SOC to use SOAR you just need repetitive work that slows your team down. MSSPs figured that out early.
You Don’t Need 20 Security Tools to Justify SOAR
One of the biggest myths around SOAR is that you need a sprawling toolset to make it “worth it.”
Not true.
Even if you only have:
- A SIEM
- An EDR
- A ticketing platform
- A few noisy alerts per day
That’s enough.
If those alerts are dragging your team down, SOAR can help.
It’s not about tool quantity it’s about how much repetitive effort your analysts are spending on avoidable work.
Common Pitfalls to Avoid
SOAR can save your team a lot of time
if it’s implemented thoughtfully.
But if you skip the fundamentals or rush into it with the wrong assumptions, you could end up with more chaos than clarity.
Here are the biggest mistakes we see teams make (and how to avoid them):
1. Automating Bad Alerts
If your SIEM is generating low-quality alerts, automating them won’t fix anything it’ll just help you make bad decisions faster.
Before you connect SOAR, make sure:
- Your alert logic is solid
- You’ve reviewed what’s being sent into your workflows
- You’re not feeding garbage into your automation
Bad input = bad output. Faster.
2. Rushing Into Too Many Playbooks
Trying to automate everything at once is a recipe for failure.
Start with 1–2 high-value, low-risk workflows like phishing triage or alert enrichment.
Get those right, then build from there.
Too many unfinished or untested playbooks can:
- Confuse your analysts
- Undermine trust in the system
- Break things quietly in the background
3. Not Defining Success (KPIs)
If you don’t know what success looks like, you won’t know if your SOAR rollout is working.
Some solid metrics to start with:
- Time saved per use case
- MTTR (Mean Time to Respond)
- Analyst workload reduction
- Number of alerts handled automatically
Having KPIs keeps the project focused and helps you justify further investment.
4. No One Owns the Workflows
Every playbook needs an owner.
Without that, updates won’t happen, logic gets stale, and people stop trusting the automation.
Assign someone to:
- Monitor performance
- Tune logic as the environment changes
- Document what the playbook does
- Be the go-to person when things need a fix
5. Forgetting to Revisit and Test Regularly
Playbooks aren’t “set it and forget it.”
Your environment changes. New tools come in. Old ones get updated. If you’re not reviewing and testing your automations on a regular basis, they’ll eventually break or worse, they’ll act on outdated logic.
Schedule regular playbook reviews.
Even 30 minutes a month can prevent major issues down the line.
SOAR isn’t about fancy features, it’s about giving your team back its most precious resource: time. By connecting your tools, enriching alerts, and running repeatable playbooks, SOAR turns endless manual tasks into quick, consistent responses.
You don’t need to automate everything at once. Pick a single pain point (phishing, malware containment, alert enrichment), build a playbook, measure success—and watch the value grow from there.
Today’s SOAR platforms work for teams big and small, with modest budgets. Start small, test often, and empower your analysts to focus on real threats, not noise.
Ready to reclaim your team’s time? Book a call, and see how CyberQuell can help you automate smarter and respond faster.