If you’ve been paying attention to cybersecurity trends, you’ve probably heard the term Zero Trust more times than you can count. But here’s the thing — it’s not just a buzzword or a passing trend. With today’s evolving threat landscape and the rise of hybrid work, Zero Trust has become an absolute must-have for any organization serious about security.
The way we work has changed. Employees aren’t always sitting safely behind a corporate firewall anymore. They’re working from home, on the go, or using their own devices. That means the old “trust but verify” approach doesn’t cut it anymore. You need to assume nothing is trustworthy by default, and that’s exactly what Zero Trust is all about.
This is where Microsoft 365 steps in as a game-changer. It’s not just a suite of productivity tools — it’s built with security at its core, designed to help you implement a Zero Trust model across your users, devices, apps, and data — all in one place.
Understanding Zero Trust: Principles and Pillars
Before we dive into how to set up Zero Trust with Microsoft 365, it’s important to understand what Zero Trust actually means.
At its core, Zero Trust is simple: never trust, always verify. That means instead of automatically trusting anyone inside your network, you verify every user, every device, and every request—every time. No exceptions.
Think of it like airport security. Just because someone has a boarding pass and made it past the first checkpoint doesn’t mean they get to walk freely everywhere. They still need to show ID, go through scans, and sometimes get extra checks before they board. Zero Trust applies this same logic to your network and data.
Zero Trust is built on six key pillars that work together to protect your organization:
- Identity: Verifying that the person trying to access resources is who they say they are.
- Devices: Ensuring the devices accessing your network are secure and compliant.
- Applications: Controlling which apps can access your data and how they’re used.
- Data: Protecting sensitive data no matter where it lives or travels.
- Infrastructure: Securing your servers, cloud services, and other backend systems.
- Networks: Monitoring and managing network traffic, both inside and outside your environment.
When these pillars work in harmony, you create a security model that’s much harder for attackers to bypass.
Why Microsoft 365 Is Built for Zero Trust
So, why is Microsoft 365 such a good fit for building a Zero Trust security setup? The answer lies in its identity-first security model.
Microsoft 365 is designed to focus on who is accessing your resources before anything else. It brings together users, devices, and apps under one umbrella, making it easier to verify every access request — which is exactly what Zero Trust calls for.
Here are some key features in Microsoft 365 that line up perfectly with the Zero Trust pillars:
- Azure Active Directory (Azure AD) Conditional Access: This lets you set rules that control access based on who the user is, where they’re accessing from, and the health of their device. For example, you can require multi-factor authentication (MFA) or block access from risky locations automatically.
- Microsoft Defender for Endpoint & Cloud Apps: These tools help you detect, investigate, and respond to threats on devices and cloud services. They continuously monitor for suspicious activity so you can act fast.
- Information Protection (Azure Information Protection and Microsoft Purview): Protect your sensitive data by classifying and labeling it, controlling who can view or share it, and tracking its usage.
- Endpoint Manager (Intune): Manage and secure the devices your users access Microsoft 365 from. You can enforce policies, keep devices updated, and even wipe data if a device gets lost or stolen.
With Microsoft 365, you don’t need to stitch together multiple tools or vendors — it’s an integrated platform designed to help you put Zero Trust into practice effectively and efficiently.
The 5 Core Implementation Areas for Zero Trust with Microsoft 365
Implementing Zero Trust with Microsoft 365 means focusing on a few key areas where security really matters. Let’s break down the five core areas you need to address, why they’re important, and how you can set them up — plus some common challenges and how to avoid them.
a. Identity & Access Management (IAM)
Feature overview:
This is all about controlling who gets in and what they can do. Azure Active Directory (Azure AD) handles user identities, while Conditional Access lets you set rules for access. Multi-factor authentication (MFA) adds an extra layer of security, and Identity Governance helps manage user roles and permissions.
Why it matters:
Since identities are the front door, if you don’t verify them properly, attackers can easily get in.
How to configure:
- Set up MFA for all users.
- Use Conditional Access policies to block risky sign-ins or require extra verification.
- Regularly review user access with Identity Governance to remove unnecessary permissions.
Common challenges + mitigation:
Users might find MFA annoying — reduce friction by using conditional policies that only trigger MFA when needed. Keep communication clear to help with adoption.
b. Device Trust
Feature overview:
Device compliance policies in Intune and Microsoft Defender for Endpoint ensure only healthy, secure devices access your network.
Why it matters:
An infected or outdated device can be an easy entry point for attackers.
How to configure:
- Enforce compliance policies (like patching, encryption, antivirus).
- Use Defender to detect threats on devices.
- Block or limit access for non-compliant devices via Conditional Access.
Common challenges + mitigation:
Managing diverse devices (BYOD) can be tough; focus on setting clear policies and provide support for compliance.
c. App and SaaS Access Control
Feature overview:
Microsoft Defender for Cloud Apps helps you monitor app usage, control sessions, and uncover shadow IT (apps running without IT knowledge).
Why it matters:
Not all apps are created equal — unmanaged or risky apps can leak data or introduce vulnerabilities.
How to configure:
- Use app discovery to identify unsanctioned apps.
- Set session controls to limit risky app activities.
- Block or restrict apps that don’t meet security standards.
Common challenges + mitigation:
Users may resist restrictions; balance security with usability by prioritizing high-risk apps first.
d. Data Protection & Sensitivity Labeling
Feature overview:
Purview Information Protection lets you classify, label, and protect sensitive data automatically. Data Loss Prevention (DLP) policies stop data from leaving your organization improperly.
Why it matters:
Even with strong access controls, data can still be accidentally or maliciously exposed.
How to configure:
- Define sensitivity labels based on data types.
- Enable auto-labeling for common sensitive content.
- Set DLP policies to block or warn on risky data transfers.
Common challenges + mitigation:
Labeling too aggressively can frustrate users. Start simple, then expand as everyone gets comfortable.
e. Network & Infrastructure Controls
Feature overview:
Modern Zero Trust often means ditching traditional VPNs in favor of more secure, flexible options like VPN-less access and micro-segmentation using Entra and Azure networking.
Why it matters:
Network-level security helps isolate threats and limits lateral movement inside your environment.
How to configure:
- Implement private access controls with Azure Entra.
- Use micro-segmentation to restrict network traffic between resources.
- Adopt VPN alternatives like Microsoft’s secure access solutions.
Common challenges + mitigation:
Network redesign can be complex. Start small with critical segments and expand gradually.
This framework helps you cover the most important Zero Trust areas without getting overwhelmed. Next, we’ll look at best practices for ongoing management and keeping your Zero Trust setup effective over time.
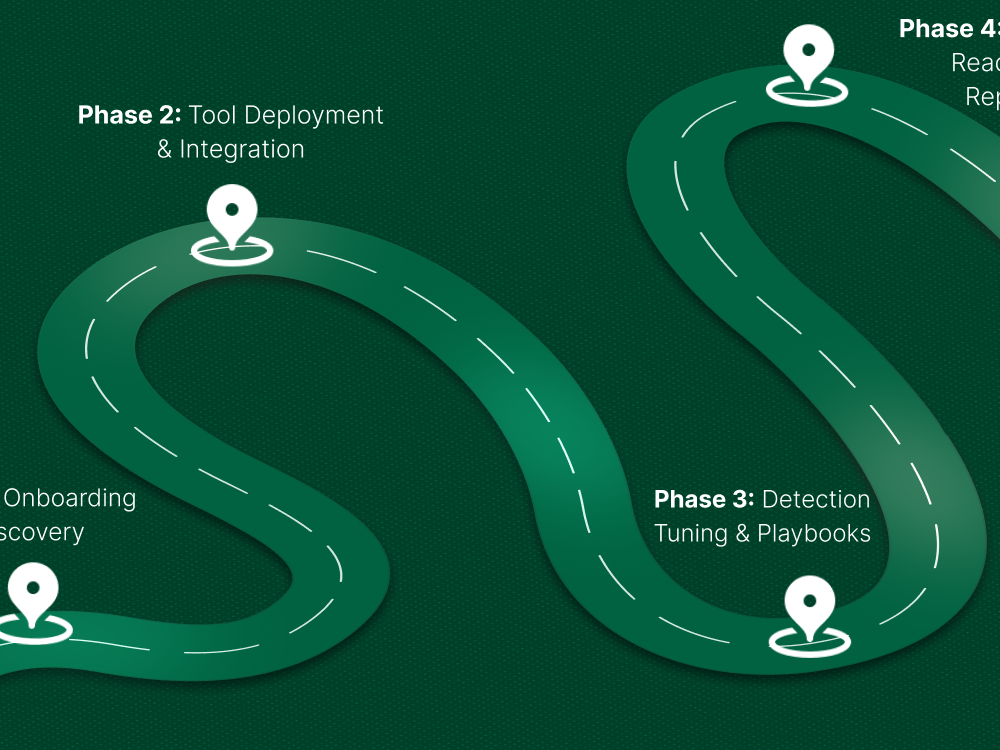
The Roadmap: Phased Rollout of Zero Trust in Microsoft 365
Implementing Zero Trust can feel like a big task — but breaking it down into manageable phases makes it way easier to handle. Here’s a simple roadmap to guide your journey, with tools and tips to keep you on track.
Phase 1: Assess Your Current Posture
Before jumping in, understand where you stand today. Use Microsoft tools like Secure Score and Compliance Manager to get a clear picture of your security strengths and gaps. These tools highlight which areas need immediate attention and where you can improve step-by-step.
Phase 2: Prioritize Identities and Devices
Start with the foundation: identity and device management. Make sure you’re protecting the who and the what—your users and their devices. Enable MFA, configure Conditional Access policies, and set device compliance rules. This phase greatly reduces your biggest attack surface.
Phase 3: Protect Applications and Data
Next, focus on what users are accessing. Lock down applications with session controls and visibility through Defender for Cloud Apps. At the same time, classify and protect sensitive data with Purview Information Protection and DLP policies. This ensures critical info stays safe, even if someone gets in.
Phase 4: Automate Enforcement, Monitoring, and Reporting
Once you have the basics covered, automate as much as possible. Set up ongoing monitoring with Microsoft Defender, automate policy enforcement, and use reporting tools to keep an eye on your security posture. Automation helps you stay ahead of threats without burning out your team.
Sample Implementation Timeline and Team Recommendations
- Month 1-2: Assessment & planning with security and IT teams.
- Month 3-4: Roll out identity and device controls.
- Month 5-6: Protect apps and data.
- Month 7+: Automate and optimize.
For smaller teams, consider involving a managed service provider (MSP) to help with deployment and monitoring. Larger enterprises might assign dedicated roles across security, compliance, and IT infrastructure.
Taking it one step at a time helps build a strong, sustainable Zero Trust setup that adapts as your organization grows and evolves.
Compliance Alignment: Mapping Microsoft 365 Zero Trust Features to Regulatory Needs
One of the big reasons organizations adopt Zero Trust is to help meet regulatory requirements — and Microsoft 365 has plenty of tools that make that easier.
Industry Examples:
- Financial: Regulations like SOX and GLBA require strict controls over data access and financial records.
- Healthcare: HIPAA demands strong protection of patient health information.
- Government: Standards like CJIS and FedRAMP focus on securing criminal justice data and federal cloud environments.
- Global: GDPR emphasizes data privacy and control for anyone handling European personal data.
Mapping Zero Trust Controls to Compliance:
Zero Trust principles naturally align with these frameworks. For example:
- Identity & Access Management ensures only authorized users access sensitive data, supporting privacy and access requirements.
- Data Protection & Sensitivity Labeling helps classify and safeguard regulated information.
- Monitoring and Reporting capabilities provide the audit trails regulators expect.
Microsoft 365 features like Azure AD Conditional Access, Purview Information Protection, and Defender tools can be configured to address many compliance controls directly.
Using Compliance Manager and Purview to Prove Governance:
Microsoft’s Compliance Manager provides an easy-to-understand dashboard showing your compliance status and improvement areas — a huge help during audits. Meanwhile, Purview tracks data classification and handling, making it simpler to demonstrate that you’re protecting sensitive information as required.
In short, implementing Zero Trust on Microsoft 365 doesn’t just boost your security — it helps check the boxes for regulatory compliance too, making life easier for your security and compliance teams.
Real-World Example: How an Enterprise Implemented Zero Trust Using Microsoft 365
Seeing how Zero Trust works in real life can make it much clearer. Here’s a walkthrough inspired by Microsoft’s own guidance and case studies on implementing Zero Trust with Microsoft 365.
Initial Risk
This enterprise faced a growing challenge: remote work had increased risks with users accessing data from personal and unmanaged devices. Phishing attacks and unauthorized access attempts were on the rise, and the company needed to strengthen its security quickly to meet compliance demands.
Implementation Approach
Following Microsoft’s recommended Zero Trust framework (Microsoft Zero Trust deployment guide), they began by assessing their environment using Microsoft Secure Score (Secure Score documentation) to identify priority areas.
They implemented Azure AD Conditional Access and enforced Multi-Factor Authentication (MFA) to tighten identity and access management (Conditional Access overview).
Next, device trust was enhanced by deploying Microsoft Intune for compliance policies and Microsoft Defender for Endpoint for endpoint protection (Intune documentation, Defender for Endpoint overview).
For data protection, the team leveraged Microsoft Purview Information Protection labels and configured Data Loss Prevention (DLP) policies to safeguard sensitive information (Purview info protection, DLP in Microsoft 365).
Finally, they set up continuous monitoring and alerts using Microsoft Defender Security Center to maintain situational awareness (Defender Security Center).
Outcomes
- Security Posture: Improved significantly — risky sign-ins dropped by over 60%, and multiple phishing attempts were blocked proactively.
- User Experience: Thanks to phased rollouts and clear communication, users adapted well to MFA and device compliance checks with minimal disruption.
- Compliance Readiness: The security and compliance teams found audit preparation easier due to detailed logs and reports provided by Microsoft tools.
Challenges Faced and Lessons Learned
The company learned that user education and training are crucial; technology alone isn’t enough. Fine-tuning Conditional Access policies helped balance security and user convenience. Most importantly, maintaining continuous monitoring proved essential — Zero Trust isn’t a one-time project, but an ongoing process.
Top Mistakes to Avoid When Implementing Zero Trust
Implementing Zero Trust isn’t just about flipping a switch — there are some common missteps that can hold you back. Knowing these upfront can save you time, headaches, and security gaps.
1. Over-reliance on MFA Without Conditional Access
Multi-Factor Authentication (MFA) is great — but it’s just one piece of the puzzle. If you only require MFA and don’t set up Conditional Access policies, you miss out on controlling when and how users access resources. That can leave holes open for risky sign-ins or compromised devices.
2. Incomplete Device Enrollment
Zero Trust depends heavily on trusting devices as much as users. Skipping or delaying full device enrollment in Intune or Defender leaves gaps in device visibility and compliance enforcement, which attackers can exploit.
3. Misconfiguring Data Labels or DLP Policies
Data protection is only as strong as its setup. Incorrectly applied sensitivity labels or lax Data Loss Prevention (DLP) rules can mean sensitive files are unprotected or alerts don’t trigger when they should. Make sure your policies align clearly with your data classification strategy.
4. Not Involving Key Stakeholders Early
Security isn’t just IT’s job. Leaving out compliance teams, HR, or business leaders can cause policy conflicts, resistance, or missed regulatory requirements. Early collaboration ensures smoother implementation and broader buy-in.
5. No Roadmap for Continuous Improvement
Zero Trust isn’t a “set it and forget it” project. Threats evolve, and so should your controls. Without a plan for ongoing monitoring, reassessment, and tuning, your Zero Trust posture will degrade over time.
Ongoing Monitoring and Optimization: Zero Trust is Not a One-Time Setup
Implementing Zero Trust with Microsoft 365 is a great start — but it’s just the beginning. To keep your security strong, you need ongoing monitoring and regular tune-ups.
The Role of Microsoft Secure Score, Audit Logs, and Alerts
Think of Microsoft Secure Score as your security health check. It highlights where you’re doing well and what needs attention. Alongside this, audit logs and security alerts give you a real-time view of what’s happening in your environment, so you can spot suspicious activity early and act fast.
How to Iterate and Improve Policies
Zero Trust isn’t “set it and forget it.” Regularly review your Conditional Access policies, data labels, and device compliance rules. If something isn’t working or if threats evolve, update your controls accordingly. Small, continuous improvements go a long way.
Importance of User Training and Change Management
Even the best tools don’t work without people. Keep your users informed and trained about security best practices and changes. When users understand why policies are in place, they’re more likely to follow them — which makes everyone safer.
Role of Automation with Microsoft Sentinel and Power Automate
Automation can take some weight off your team. Tools like Microsoft Sentinel help automate threat detection and response, while Power Automate can streamline repetitive tasks like notifications or policy enforcement. This means faster reaction times and more consistent security.
How Cyberquell Can Accelerate Your Zero Trust Journey
Building and maintaining a strong Zero Trust setup can feel overwhelming — that’s where Cyberquell steps in to help.
Our Approach: Assessment → Implementation → Optimization
We start by assessing your current security posture, pinpointing gaps and priorities. Then, we help implement tailored Zero Trust controls within Microsoft 365, making sure everything fits your unique environment. Finally, we stay involved to optimize and fine-tune your setup as your needs evolve.
Industry-Specific Deployment Experience
Every industry has its own challenges and compliance needs. Whether you’re in finance, healthcare, government, or any other regulated space, we bring the experience to align Zero Trust with your specific requirements.
Dedicated Support and Microsoft 365 Certified Experts
Our team of certified Microsoft 365 specialists is here to guide you every step of the way — from technical configuration to user training and ongoing support.
Zero Trust is no longer optional — it’s essential in today’s evolving security landscape. Microsoft 365 provides a comprehensive platform to build a robust Zero Trust architecture that protects your identities, devices, applications, and data wherever they are. By embracing this approach, you reduce risk, improve compliance, and create a security posture that can adapt as threats evolve.
If you haven’t started yet, now is the time to assess your current security setup and take the first step toward Zero Trust with Microsoft 365. Don’t wait for a breach to push you into action. Reach out for a detailed security audit or consultation to understand your readiness and get expert help designing a plan that works for your business. Stronger security starts with one confident step — take it today.