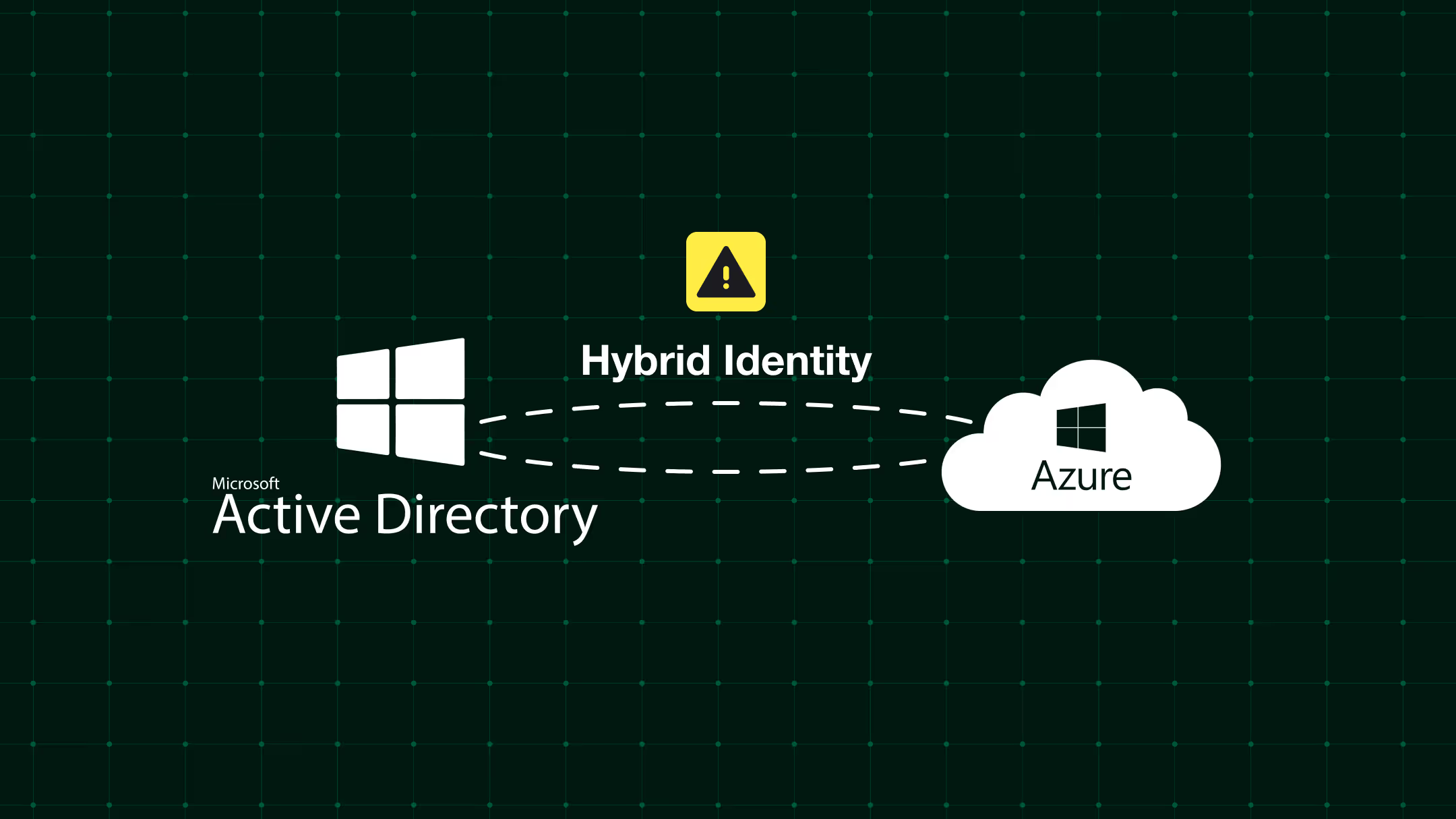
Most IT teams don’t spend much time thinking about hybrid identity once it’s up and running. And honestly? That’s fair. Syncing your on-prem Active Directory with Azure AD just works. Users can log in, their passwords match, and things hum along quietly in the background.
But attackers don’t forget about it. In fact, they love that you do.
The truth is, hybrid identity is one of the most overlooked entry points in enterprise environments. It’s not flashy. It’s not new. But it quietly connects two very different worlds: your old-school AD and your modern cloud setup and if it’s misconfigured, it can open doors you didn’t even know existed.
So, What Is Hybrid Identity Exactly?
You’ve got an old-school Active Directory running in your data center. And you’ve also got Azure AD (now called Microsoft Entra ID) handling cloud apps like Microsoft 365, Teams, and others.
Hybrid identity is the setup that keeps those two worlds connected. It’s the bridge that lets users sign in once and use both systems, without managing two separate accounts.
It’s what makes things like single sign-on (SSO) work across your on-prem apps and your cloud services. And it does that by syncing accounts between AD and Azure AD, so passwords, group memberships, and user info stay aligned.
The usual tools involved include:
- Azure AD Connect, which handles the sync between on-prem AD and Entra ID
- Cloud Sync, a lighter alternative for simpler setups
- Password Hash Sync (PHS), which copies password hashes to the cloud
- Pass-Through Authentication (PTA), which checks passwords on-prem for added control
It all sounds smooth, and when it’s set up right, it is.
But here’s the problem: most teams set it up once and never look at it again. Over time, misconfigurations creep in, accounts end up with too many permissions, and no one notices that the sync bridge has a few cracks.
And attackers? They’re looking right at those cracks.
Where Things Start to Break (Real-World Risks)
Hybrid identity sounds great on paper. But the reality? It’s full of small cracks that can turn into big problems if you’re not paying attention.
Here are a few of the most common ones:
Privileged accounts getting synced to the cloud by mistake.
Let’s say your domain admins are included in the sync scope. Now their credentials live in the cloud, possibly without the same protections you'd have on-prem. If those accounts get compromised, attackers have a foot in both worlds.
Soft match errors.
This happens when Azure AD tries to match a cloud user to an on-prem user based on their email or UPN. If there’s overlap or a mismatch, it might accidentally merge the wrong accounts. That can mean unintended access or even overwriting existing permissions.
Azure AD Connect server compromise.
The sync server is often treated like “just another box” but it holds the keys to your directory. If an attacker gets onto that machine, they can extract credentials, modify sync rules, or open a path straight into Azure AD.
Legacy protocols sneaking around MFA.
Protocols like POP3, IMAP, or SMTP don’t support modern authentication. If they’re still enabled, users (or attackers) can bypass MFA completely. All it takes is one user with a weak password using an outdated email client.
How to Design Hybrid Identity Without Opening Security Holes
Let’s be honest. Most hybrid identity setups are built once and then left alone. That’s where the problems usually begin.
If you want to keep things secure, it helps to be intentional from the start. That means picking the right sync method, setting clear rules, and locking down the systems that matter.
Start with the right sync model
Don’t just go with the default. Understand what you're using and why.
- Password Hash Sync (PHS) is great for most cases. It’s simple and supports cloud-based sign-in with better visibility.
- Pass-Through Authentication (PTA) keeps password checks on-prem, which gives more control in some scenarios.
- Cloud Sync is lighter and works well for basic or branch office setups.
Each one solves a different problem. What matters is choosing the one that actually fits your environment.
Filter what gets synced
This is where many teams go wrong. Syncing everything might seem easy, but it’s risky.
- Don’t sync Domain Admins or Enterprise Admins
- Leave out service accounts and old test accounts
- Review what’s being synced regularly to keep the scope tight
Smaller sync scope means fewer potential entry points for attackers.
Fix your UPNs and email address alignment
If usernames or email formats are different in AD and Azure AD, sync can break. Worse, it might merge two unrelated accounts. Make sure user attributes are consistent across both environments before you sync.
Secure your Azure AD Connect server
This machine often gets overlooked, but it holds serious power. Treat it like critical infrastructure.
- No internet access
- No remote desktop access from outside your secure network
- Keep it patched
- Use a dedicated service account with minimal permissions
- Limit who can log in locally
If an attacker gets access to this server, they can change sync settings, expose accounts, or quietly create back doors into Azure AD.
Most attacks don’t need advanced tools or zero-days. They just need an old server that no one’s paying attention to anymore.
Put Guardrails in Place (So You Don’t Have to Watch Everything, Always)
You can’t watch every account, every login, or every little change happening across your hybrid setup. And honestly, you shouldn’t have to.
That’s where guardrails come in. Once you put the right ones in place, you don’t need to babysit the system. The security controls do the heavy lifting for you.
Start with MFA for everyone
If users are synced from on-prem, make sure they still get prompted for multi factor authentication. It doesn’t matter if they’re logging in from the cloud or from your internal network. Every account needs that extra layer of protection.
Use Conditional Access to control who gets in, and when
Conditional Access lets you enforce smart rules that make sense for your environment. For example:
- Block legacy authentication protocols that don’t support MFA, like POP3 or IMAP
- Require trusted devices or known locations for sign-ins
- Limit access to certain apps if risk is detected
These policies work in the background and help stop risky sign-ins before they become real problems.
Turn on Identity Protection
This feature watches for unusual behavior, like sign-ins from unfamiliar locations or impossible travel. If something looks off, it can automatically block the sign-in or require MFA again.
Let Microsoft’s machine learning do what it does best spotting patterns most people miss.
Use PIM to control privileged access
Privileged Identity Management, or PIM, helps you stop handing out standing admin access. Instead, users can request elevated roles only when they need them.
- Access is temporary
- It can require approval
- You get an audit trail of who did what, and when
This cuts down your attack surface and helps you avoid “forgotten admin accounts” that sit quietly with too many permissions.
Once these controls are in place, you don’t have to keep watching everything manually. You’ll have systems working in your favor, flagging problems early and limiting the damage when something goes wrong.
Monitor What’s Going On Even If It’s Boring
Monitoring might not be the most exciting part of hybrid identity security, but it’s where a lot of issues start to show up. And if you’re not watching, they’ll slip past unnoticed.
This doesn’t mean staring at dashboards all day. It just means setting up the right tools to keep an eye on the basics and alert you when something’s off.
Start with Azure AD Connect Health
This tool gives you visibility into your sync process. You can:
- Catch sync failures before they become help desk tickets
- Spot credential issues or changes in the sync schedule
- Get alerted when the sync server goes down or stops working properly
It’s easy to set up and can save hours of troubleshooting when something breaks.
Keep an eye on your sign-in logs
Your Azure sign-in logs are full of clues. Look for things like:
- Impossible travel (user signs in from New York and Singapore five minutes apart)
- Brute-force attempts or multiple failed logins from unfamiliar IPs
- New sign-ins from unexpected locations or devices
These signals often show up before a real breach happens.
Clean up group memberships and user attributes
Over time, users get added to groups they don’t need, and attributes like department or title fall out of sync. That may not seem urgent, but over-permissioned users are a huge risk.
If someone gets compromised, the last thing you want is for them to have more access than necessary.
Watch what you’re syncing
If your directory is full of stale users, test accounts, or poorly labeled groups, you’re just asking for confusion. Or worse, you’re syncing an account you forgot existed — and now it’s exposed in the cloud.
Be Ready for the ‘Oh No’ Scenario
Here’s something that surprises a lot of teams:
Azure AD Connect is not a backup.
If you accidentally delete a bunch of users on-prem and sync those changes, guess what happens in Azure AD?
Those users have gone there too.
There’s no undo button. No rollback. No safety net unless you build one yourself.
Set up a staging server for failover
Most teams skip this. But having a second Azure AD Connect server in staging mode gives you a way to recover if your primary server dies or misbehaves.
You won’t use it every day, but when you need it, you’ll be glad it’s there.
Document what happens when sync breaks
It’s not enough to have tooling. You need a human-ready plan. Ask yourself:
- Who gets notified if the sync fails?
- What’s the process to pause syncing and fix a problem?
- If user accounts get messed up, how do you restore them?
- What happens to app access while accounts are broken?
- Who’s responsible for flipping to staging mode or restoring the directory?
Even if you only answer these questions once and put it in a simple doc, that’s better than nothing. In a crisis, people don’t have time to guess.
Hybrid identity is great when it works. But when it breaks, it breaks fast. Planning for failure isn’t pessimistic, it's just part of running a system that matters.
Users Are Part of This Too
You can lock down your sync settings. You can monitor every sign-in. But if your users click the wrong thing, all of that can still fall apart.
That’s why identity security isn’t just about configuration.
It’s also about education.
Train users to:
- Watch out for weird login prompts that feel off
- Say no to MFA fatigue attacks (those repeated push notifications that wear people down)
- Spot fake Microsoft login pages or consent requests asking for access they don’t understand
It doesn’t have to be a full-blown security training program. Even a short email or a quick session during onboarding can go a long way.
Because at the end of the day, your setup is only as secure as the person behind the keyboard.
Hybrid identity isn’t going anywhere. It’s still the easiest way to bridge your on-prem AD and your cloud apps without turning everything upside down.
But let’s be clear it’s not secure by default.
It only stays safe if you:
- Choose your sync model carefully
- Filter what you sync
- Lock down the infrastructure
- Add smart guardrails like MFA and Conditional Access
- Keep an eye on what’s happening behind the scenes
You don’t need to rebuild your whole identity setup.
Just make a few targeted changes that protect the pieces attackers usually go after.
You can keep the user experience simple and smooth. And still make life a lot harder for anyone trying to sneak in.
Most hybrid identity setups look fine on the surface until someone takes a closer look.
At Cyberquell, we help IT and security teams find what usually slips through the cracks. That means over-synced accounts, weak spots in Azure AD Connect, and identity risks that attackers quietly look for.
No pressure. No sales call. Just a practical, human-readable risk review of your hybrid identity setup.
If you want to stop guessing and see what’s actually exposed, we can help. Book a call, and we’ll help you get started